My IP ↗or
My IP ↗orAs businesses expand their digital footprints, online fraud and malicious traffic have grown increasingly sophisticated. VPNs, proxies, private relays, and other anonymization tools are being adopted widely — not only by legitimate users for privacy, but also by fraudsters aiming to bypass security measures. IPinfo’s Privacy Detection API helps businesses accurately identify and mitigate these hidden threats, ensuring secure transactions, compliance, and reliable user experiences.
Keeping ecommerce, gametech, and fintech websites secure, for instance, requires staying one step ahead of malicious traffic.
This task is even more difficult since fraudulent users typically mask their identities. The result is that malicious traffic seems to have the upper hand… if it weren’t for privacy detection data.
Hidden Identities: What Does That Mean?
Anonymous users conceal their identities using several common methods. Here's a brief overview of the primary techniques:
Virtual Private Networks
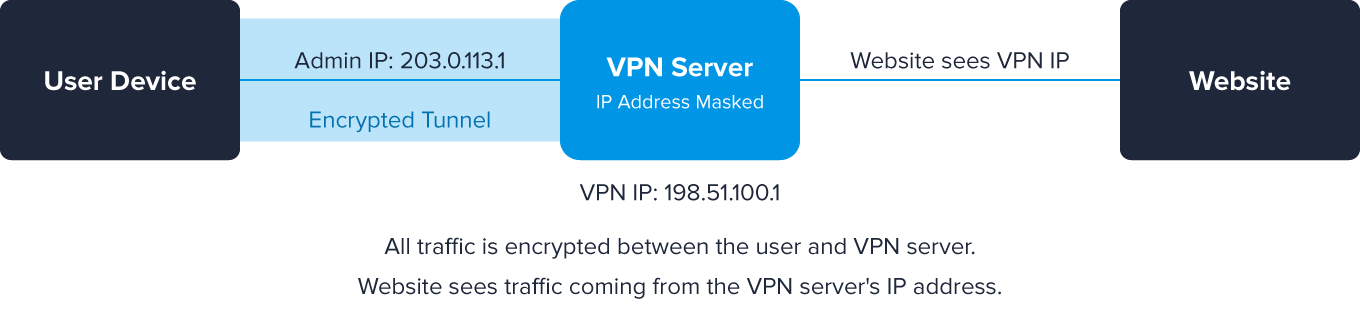
VPNs loan users a temporary IP address while encrypting their real location details. The result is that websites or ISPs can’t track identities or geolocation data.
What does this mean for malicious traffic? For one, scammers go undetected, and they gather information without alerting website owners. VPN users also try to outsmart online streaming policies that reserve content for certain territories or countries. In fact, that’s why services such as Hulu want to block VPN traffic to protect their bottom line.
That being said, VPNs aren’t all bad. They can also protect IPs from hackers who break into networks and take over devices using network connections. In short, VPNs can be used for good or bad depending on users’ intentions.
For legitimate users, VPNs protect privacy and secure communications. However, malicious actors use VPNs to:
- Evade detection while gathering sensitive information
- Bypass regional content restrictions on streaming platforms
- Conduct fraudulent transactions from locations that appear legitimate
- Circumvent IP-based security measures
Tor Usage
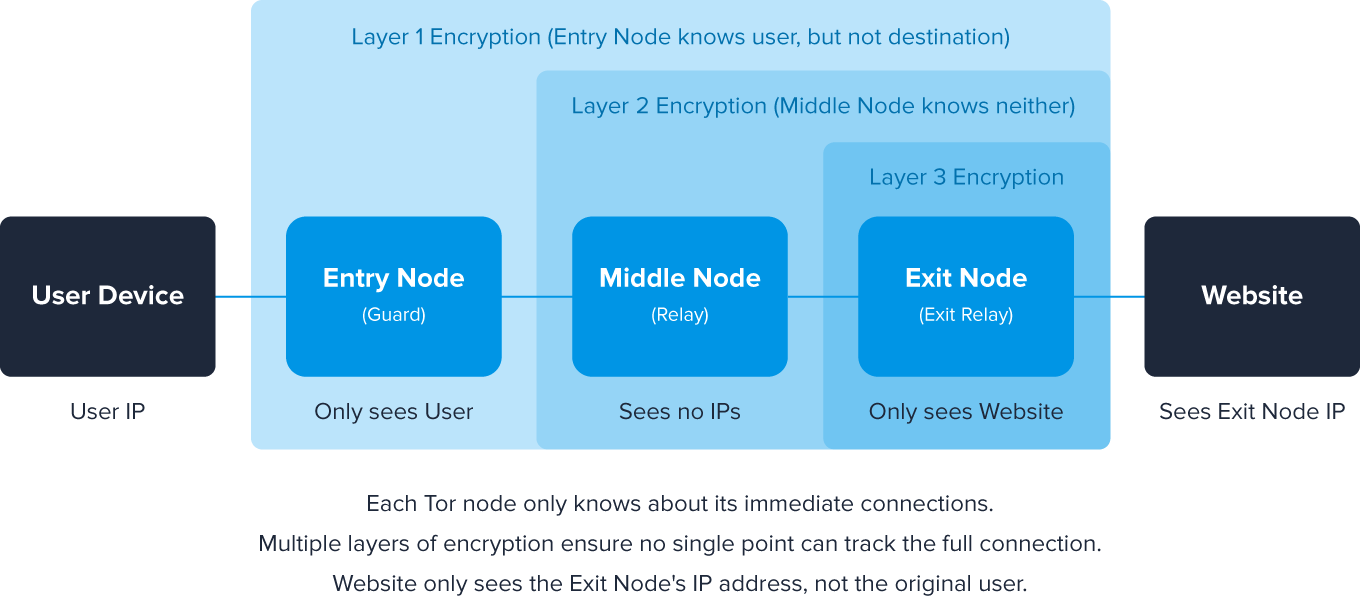
Another source of anonymous traffic is Tor usage. Tor users can effectively conceal geolocation information and usage from those who conduct traffic analysis. This free and open-source software can then be used to hack into networks, conduct cyber attacks, and even take over websites.
How does it work? Tor is a traffic relay system run by thousands of volunteers around the world. And while this software may slow down browsing speeds, it also protects anonymity better than VPNs.
Interestingly, this anonymous communication system was originally created by the US Navy. But in recent years, it has attracted more and more fraudulent activity.
While Tor has legitimate privacy applications, it's increasingly utilized for:
- Concealing cyber attack origins
- Accessing dark web marketplaces
- Bypassing sophisticated network monitoring systems
- Conducting anonymous transactions
Proxies
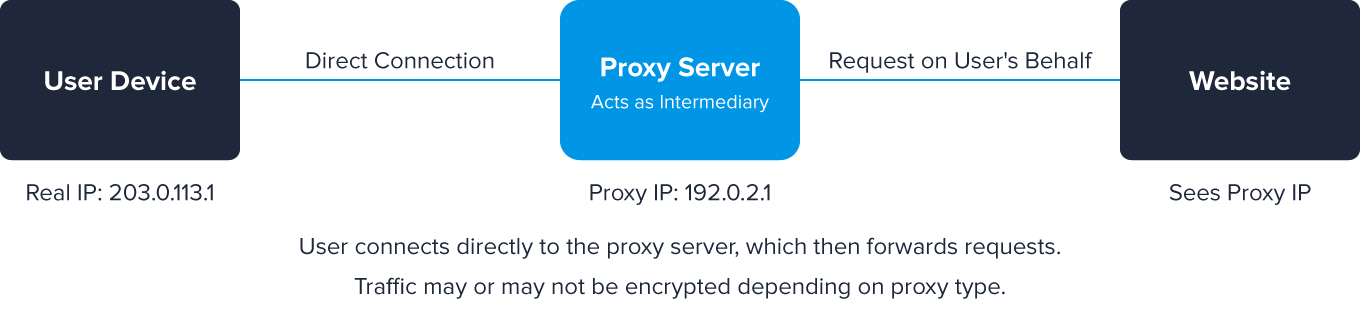
Proxies work much like VPNs. On the bright side, these servers can be set up as firewalls or web filters, protecting individual devices. However, like the examples listed above, they’re also used for fraudulent activity.
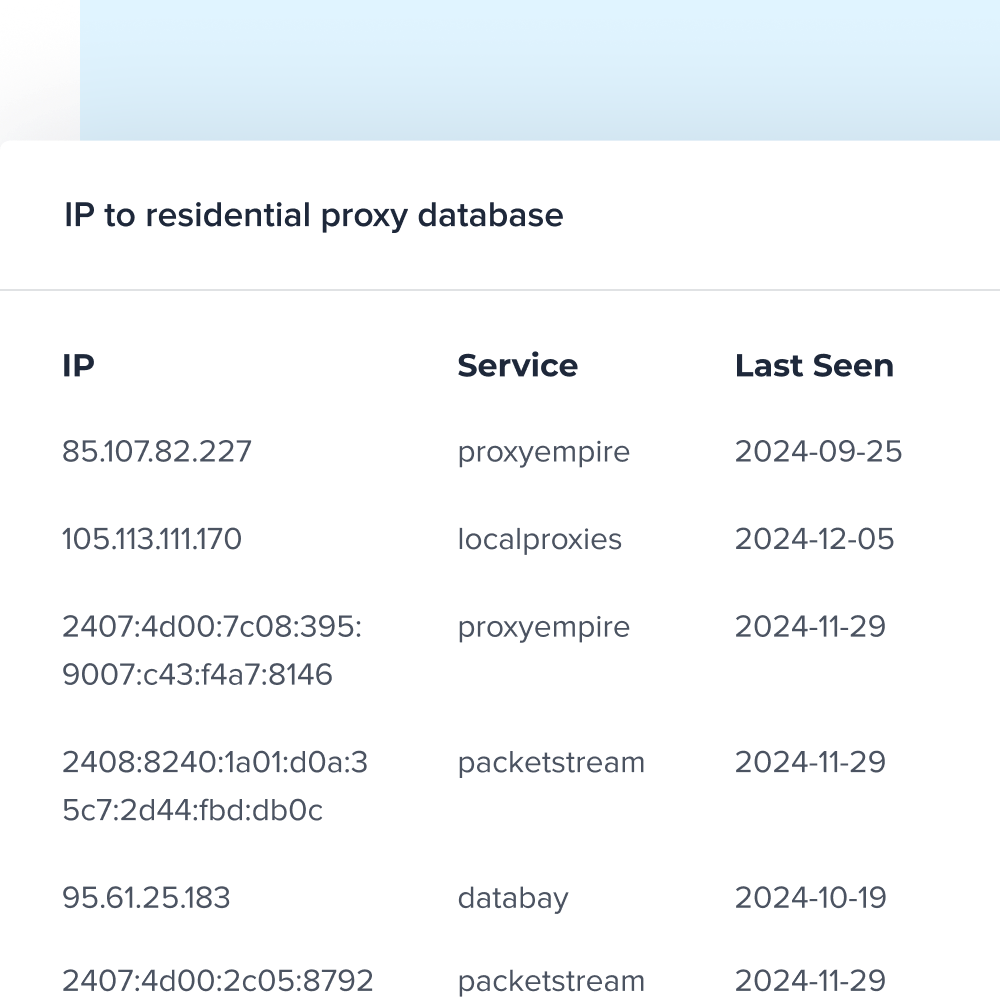
A user in Brazil, for instance, can hide their true geolocation information by using a proxy located in France or some other place. And since the data will be coming from a third party, websites won’t be able to track IP addresses. Learn more about the rising popularity of residential proxies.
This technique is commonly employed to:
- Bypass geo-restrictions
- Hide web scraping activities
- Conduct automated attacks without revealing the source
- Test website functionality from different global locations
Detect residential proxies with accurate IP data
Add a critical layer of defense to your fraud prevention and security workflows by identifying residential proxy IPs.
Connection via Hosting Provider
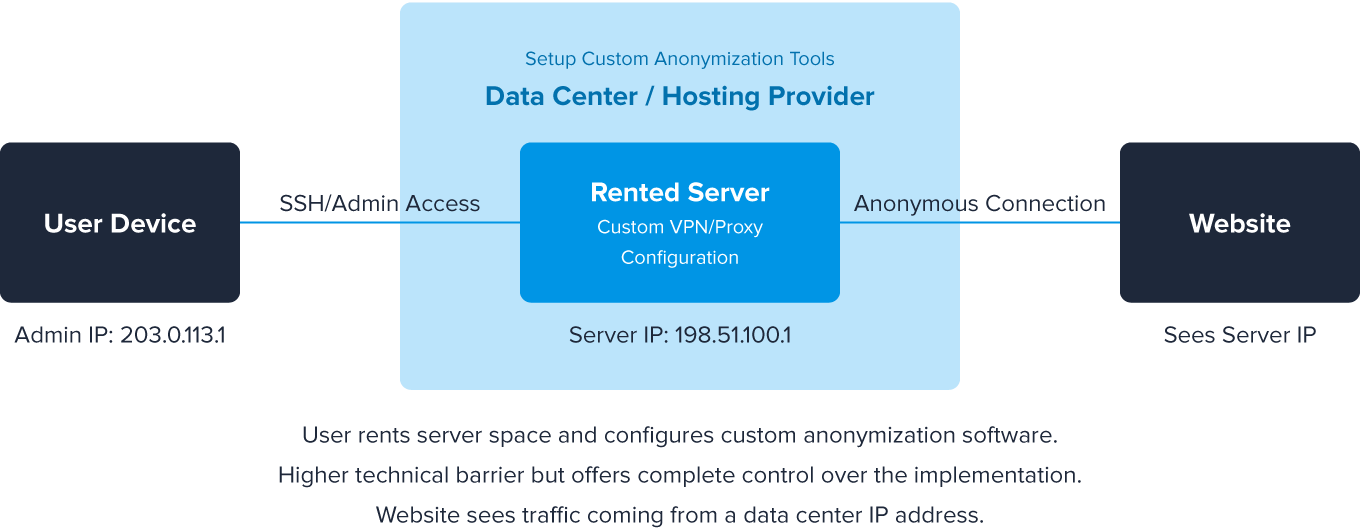
Hosting providers offer server infrastructure and connectivity for websites and applications. While most operate legitimately, some hosting environments become staging grounds for:
- Malware distribution
- Ransomware operations
- Botnet command and control centers
- Anonymous attack platforms
Private Relays
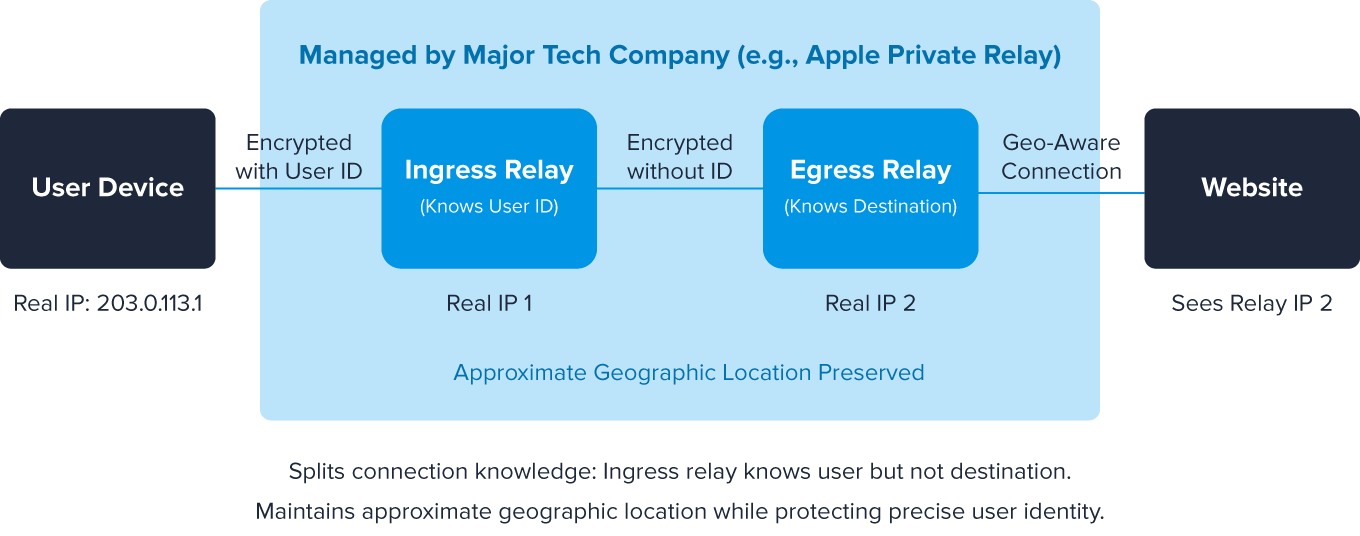
Private relays represent a newer form of privacy technology that has gained significant traction since 2023. Unlike traditional VPNs or proxies that might be used for various purposes, private relays are typically offered by major tech companies as privacy-enhancing features for their users.
Apple's iCloud Private Relay and similar services from companies like Mozilla route user traffic through two separate relay points. The first relay knows who the user is but not what site they're visiting, while the second relay knows what site is being visited but not who the user is. This dual-hop architecture provides privacy while maintaining legitimate geo-region information. Find out more about how private relays work.
Key characteristics of private relays:
- Maintain regional accuracy while masking exact user location
- Often built into popular devices and browsers
- Designed primarily for legitimate privacy protection, not circumvention
- Typically preserve some general location data for content localization
- More difficult to block without impacting legitimate users
Private relay traffic presents unique challenges because it comes from trusted providers and often represents legitimate users who are simply privacy-conscious rather than attempting to commit fraud. This requires more nuanced approaches to traffic management.
How IPinfo’s Privacy Detection API Works
The good news is that companies can stay ahead of fraudulent traffic by taking a few preventative measures. Specifically, IP address data can help companies pinpoint suspicious activity before they incur any damages.
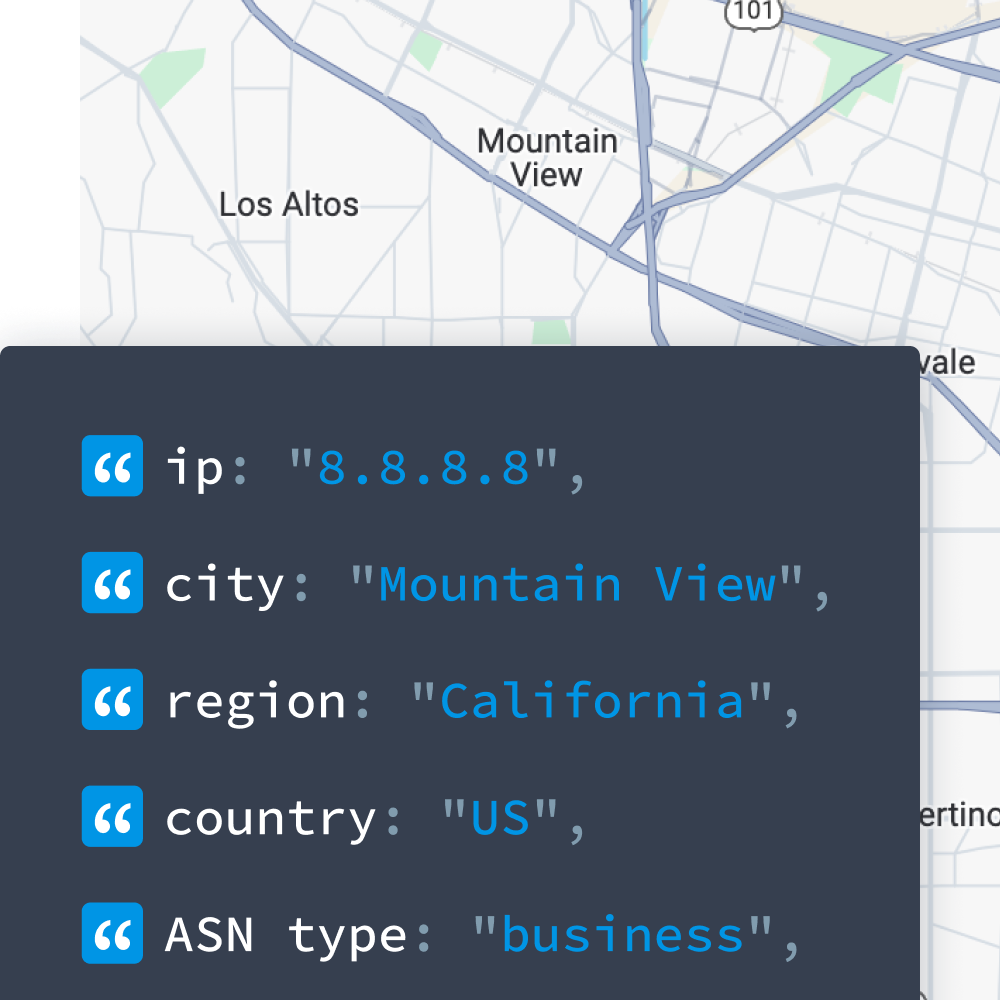
$ curl ipinfo.io/45.140.167.154/privacy?token=$TOKEN
{
{
"vpn": true,
"proxy": false,
"tor": false,
"relay": false,
"hosting": true,
"service": "VPNhack"
}Here’s what our privacy detection data is designed to do.
- Filter malicious traffic
- Block bots and spammers
- Prevent web scraping
- Enforce content restrictions
- Flag IPs masking their identity
Why IPinfo’s Privacy Detection Data Is More Accurate
IPinfo’s API performs internet-wide scans, detecting nearly 600 million IP addresses that have been associated with an anonymous IP service provider. Unlike other IP data providers, IPinfo ensures maximum accuracy through our proprietary detection methodology:
- Global Probe Network: Our infrastructure of 900+ servers across 200+ cities performs continuous internet-wide scans using ping measurements, traceroute analysis, and port scanning to map VPN endpoints.
- Active protocol verification: We conduct direct VPN handshake testing on multiple ports, successfully identifying anonymous IPs that other providers miss.
- Multi-source data integration: We combine our probe network findings with device data patterns, WHOIS information, Tor exit node registries, and public proxy lists for comprehensive coverage.
- Direct provider subscription: We maintain active subscriptions to all 180+ VPN services we track, giving us firsthand verification of their IP ranges and infrastructure changes.
- Dedicated data engineering team: Our experts continuously validate findings and refine detection algorithms through a rigorous quality assurance process.
- Daily database updates: Our systems immediately incorporate new providers, remove defunct services, and track changes in IP assignments to maintain current data.
- Zero false entries: We ensure elimination of non-existent or fake VPN providers from our database.
"We tested multiple data providers, including Maxmind. Only IPinfo consistently delivered accurate and reliable VPN detection data. IPinfo's data integrity makes a significant difference in our fraud prevention and compliance measures."
— Yonko Tsonev, Head of IT, Adcash
How Can the Privacy Detection API Be Used?
IPinfo's Privacy Detection API offers versatile applications, making it a critical tool for online security, compliance, and user experience. Here are some of the primary use cases:
Filtering Malicious Traffic
First and foremost, businesses can filter the good traffic from the bad by blocking bots, spammers, and other harmful visitors. Ecommerce, fintech, and gametech platforms especially benefit by enhancing their customer experience, minimizing disruptions, and safeguarding their digital operations against fraudulent activities.
Notably, the 2025 Imperva Bad Bot Report revealed that, for the first time, automated traffic accounted for 51% of all web traffic in 2024, with malicious bots constituting 37% of this figure. This marks the sixth consecutive year of growth in bad bot activity, posing significant challenges for organizations striving to safeguard their digital assets...
Enforcing Content and Geographical Restrictions
OTT (Over-The-Top) services deliver video and audio content directly via the internet, bypassing traditional providers. These platforms frequently implement geo-restrictions due to licensing agreements, which VPN users may attempt to circumvent by masking their location. The Privacy Detection API helps streaming services, sports broadcasters, media companies, and content providers detect VPN, proxy, or private relay usage to effectively enforce regional restrictions. Streaming giants like Netflix continually refine their strategies to maintain compliance, and similarly, live sports broadcasters leverage this technology to uphold territorial broadcasting rights, protecting both revenue and content exclusivity.
Preventing Web Scraping
Scrapers can harvest valuable content, prices, or product listings, compromising competitive advantage and affecting availability for genuine users.
Major companies such as LinkedIn have recently taken legal actions against web scraping.
IPinfo’s Privacy Detection API and Residential Proxy database equips businesses to proactively block scraping attempts by identifying and restricting traffic from proxies, hosting providers, and other anonymizing services.
Fighting Fraud
Accurate IP address detection helps businesses defend against transaction fraud and account takeovers. Recent surges in account takeovers reported by PayPal illustrate the critical need for effective fraud prevention measures. By unmasking VPN and proxy users, companies can trigger additional verification steps, like two-factor authentication, enhancing security measures. This additional layer of protection significantly reduces spam, ransomware, phishing attacks, and other cyber threats, ensuring safer online experiences for customers and greater peace of mind for businesses.
Want to learn even more about anonymous IP providers?
Read our ebook “The Essential Guide to Anonymous IPs and Privacy Detection Data.”
Get Started With IPinfo
With IPinfo's consistently updated and verified privacy data, businesses are well-equipped to address the evolving challenges posed by anonymized internet traffic, maintaining robust digital security and a trusted user experience.
IPinfo’s Privacy Detection API helps innovators in many industries stay ahead of malicious activity. The result is well-protected digital assets, safeguarded investments, and customers’ trust.
Privacy detection made easy
Prevent fraud and save money with our accurate, reliable privacy detection API. Setup takes minutes.
About the author

As the product marketing manager, Fernanda helps customers better understand how IPinfo products can serve their needs.