Fraudsters are constantly adapting to the changing digital landscape, and one of their favorite tactics is hiding their identities using VPNs, proxies, and other IP-anonymizing tools. These methods allow them to mask their true IP address, making it harder for businesses to tell the difference between legitimate users and bad actors. But to stay ahead of financial and reputational risks, identifying and addressing their behaviors quickly is key.
At IPinfo, we’ve seen firsthand how critical IP data is in identifying and stopping fraud early. Our privacy detection data helps organizations across various specialized teams (security, risk, and fraud prevention) spot suspicious activity that would otherwise fly under the radar.
In this post, we’ll break down the most common fraud schemes that rely on VPNs – and how IPinfo’s data helps companies mitigate these risks.
Common Fraud Schemes That Rely on VPNs
Some users employ VPNs for privacy. Fraudsters use them to enable large-scale fraud with low risk of getting caught. Some of the most common schemes include:
1. Account Takeovers (ATOs)
In an ATO, a bad actor gains unauthorized access to a legitimate user’s account, often through credential stuffing or phishing, and uses it for malicious purposes. VPNs help fraudsters avoid geolocation-based detection mechanisms by spoofing the original user's location.
2. Fake Sign-Ups and Bot Activity
VPNs are frequently used to create fake accounts at scale, especially when paired with automated scripts and device emulators. These fake accounts can be used for spam, bonus abuse, or to manipulate platform metrics.
3. Ad Fraud
In digital advertising, fraudsters use VPNs to simulate clicks, impressions, or installs from different locations or devices to inflate engagement and steal ad spend. Read more about how click fraud affects ad budgets.
4. Geo-Fraud
Some services, like content providers, fintech apps, or online marketplaces, are restricted by region. VPNs allow fraudsters to bypass these geo-restrictions, opening the door to abuse or non-compliance with regional regulations.
Experience best-in-class IP privacy data
With IPinfo, discovering IP addresses using anonymization tools is easier than ever.
How Privacy Detection Helps
VPN usage isn’t always fraudulent. The key is context. Businesses need to understand when privacy tools are being used in suspicious or inconsistent ways. That’s where privacy detection comes in.
What Is Privacy Detection?
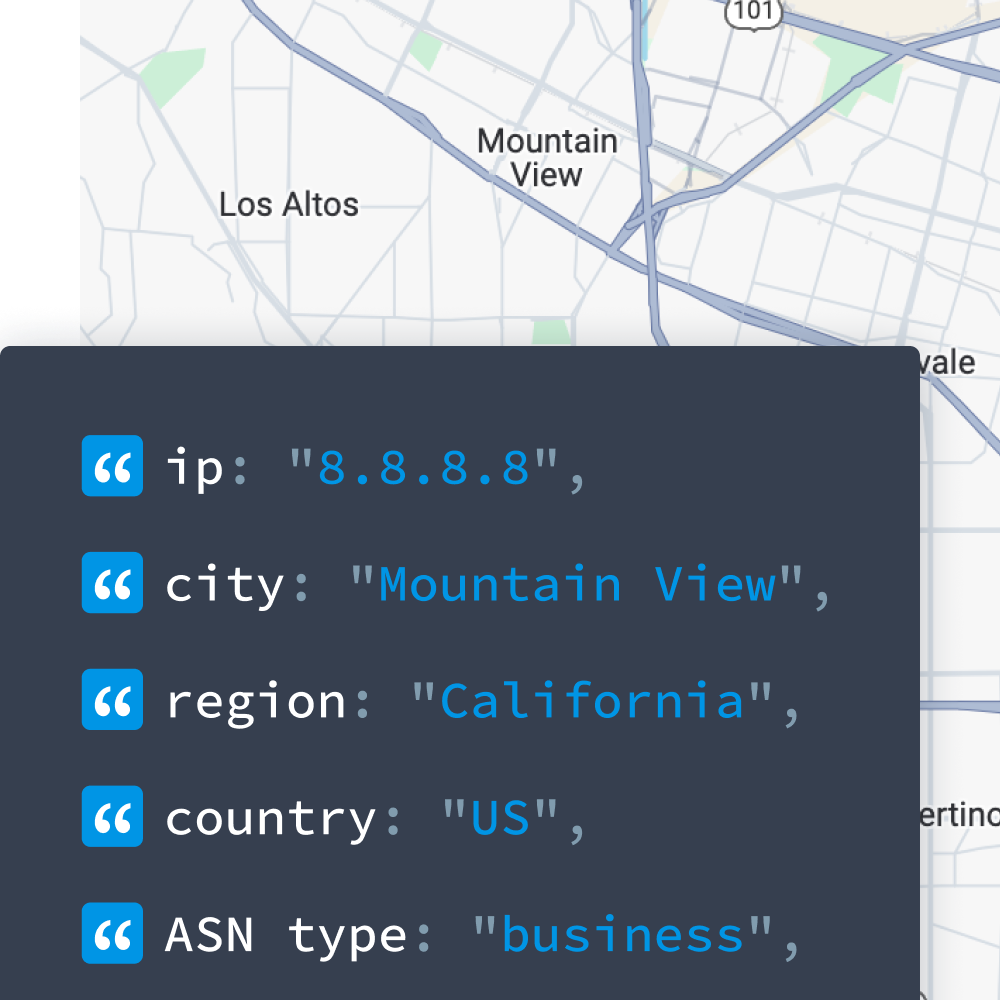
Privacy detection information like ours empowers users with more context about the IP addresses engaging with their products and services. Our data shows:
- Whether the IP is associated with a VPN, proxy, Tor, or other obfuscating service
- If an IP address is linked to a known VPN service
- What type of proxy is being used (public, residential, or other)
- What hosting provider the IP belongs to
This data can then be used to make smarter decisions in real time.
Benefits of Privacy Detection for Fraud Prevention
- Identify suspicious activity: Spotting VPN usage during account creation, login, or transaction stages helps teams flag potentially fraudulent behavior.
- Improve risk scoring: Adding privacy detection data to your risk model provides more context, allowing for better decisions without adding friction for genuine users.
- Protect geo-restricted services: Knowing when a user’s IP doesn’t match their expected location or violates regional access controls helps maintain compliance.
- Reduce fake engagement: Detecting IPs from shared VPNs or data centers can help shut down fake sign-ups or coordinated bot campaigns.
Read our ebook The Essential Guide to Anonymous IPs and Privacy Detection Data for more details about IP anonymizers.
IPinfo's Comprehensive Fraud Detection Capabilities
IPinfo offers multiple layers of IP intelligence to help organizations detect and prevent fraud effectively. Our fraud detection capabilities include:
Privacy Detection Dataset
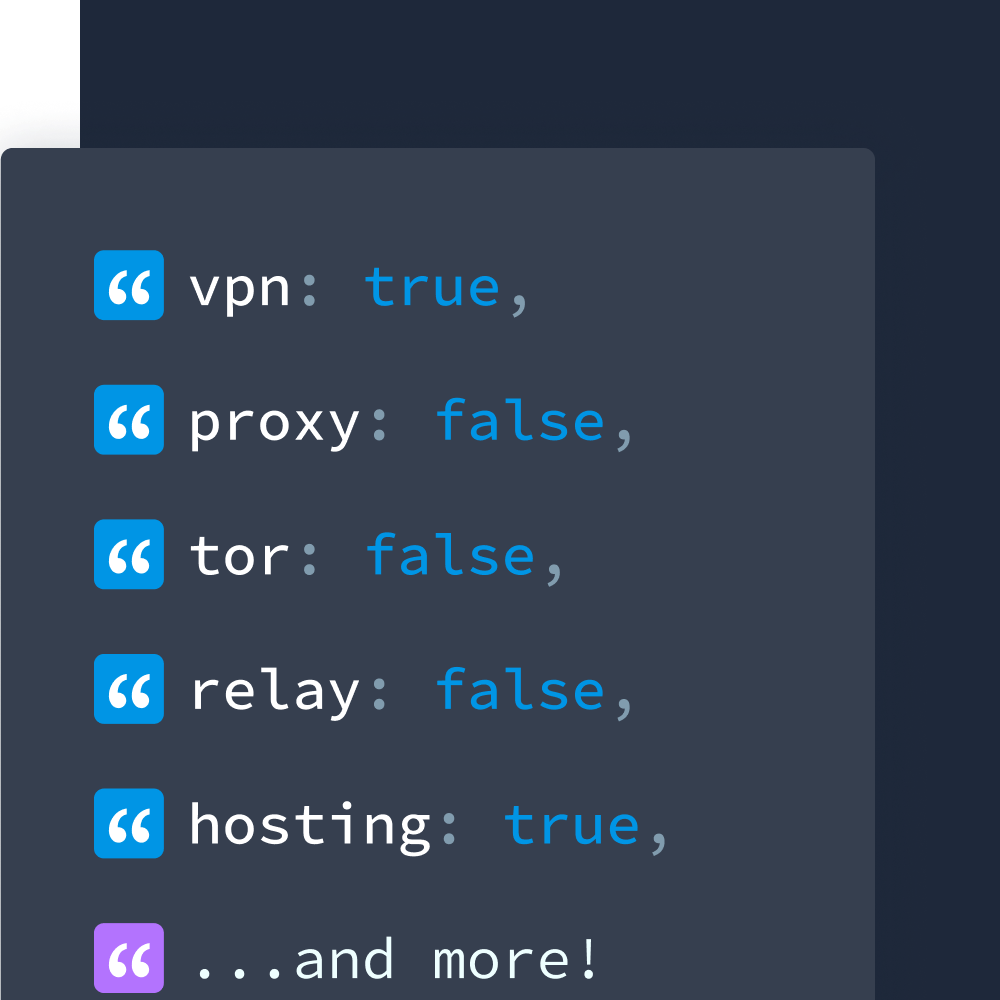
Our core Privacy Detection dataset identifies IP addresses associated with anonymization services, including:
- VPNs: Virtual Private Networks that mask users' true locations and identities
- Proxies: Intermediary servers that route traffic and hide original IP addresses
- Tor: The Onion Router network used for anonymous browsing
- Relays: Services like Apple Private Relay that provide privacy-preserving traffic routing
- Hosting/Data Centers: Server IPs that shouldn't typically be generating consumer traffic
Each IP address is evaluated against these categories with binary indicators (true/false) and includes a "service" field that identifies specific VPN providers when applicable.
Privacy Detection Extended Dataset
For organizations requiring deeper insights, our Extended dataset provides additional technical attributes that reveal exactly how we detected each anonymous IP:
- Confidence levels (1-3): Indicating our certainty about the privacy service detection
- First_seen and last_seen dates: Tracking when activity was first and most recently observed
- Coverage percentage: For inferred ranges showing what proportion has direct evidence
- Detection method indicators including:
- Census: Whether VPN protocols were detected on specific ports
- Device_activity: If we've observed VPN-like usage patterns
- VPN_config: Whether we confirmed the IP in VPN configuration files
- WHOIS: If there's a WHOIS association with established VPN providers
Residential Proxy Dataset
Our newest offering detects one of the most challenging fraud vectors: residential proxies. These are particularly dangerous because they route traffic through legitimate residential IP addresses, making them extremely difficult to detect with traditional methods.
The Residential Proxy dataset includes:
- IP address: The specific IP identified as a residential proxy
- Service: The name of the residential proxy service provider
- Last_seen: Date of most recent activity
- Percent_days_seen: Stability metric indicating frequency of detection
Data Collection Methodology
What sets IPinfo's fraud detection capabilities apart:
Comprehensive Coverage: Our data encompasses traditional VPNs, open proxies, Tor exit nodes, hosting providers, and the challenging-to-detect residential proxy networks.
Multi-layered Detection: We employ multiple methodologies rather than relying on a single detection vector:
- Active enrollment in commercial privacy services
- Internet-wide port and protocol scanning
- VPN handshake verification via our global Probe Network
- WHOIS record analysis
- Behavioral pattern recognition
- Device data correlation
Regular Updates: With 18% of privacy IP data changing weekly and 41% changing monthly, our daily updates ensure you're working with the most current information possible.
Global Perspective: Our Probe Network spans hundreds of servers worldwide, providing comprehensive visibility into global IP behaviors.
These capabilities allow organizations to implement sophisticated risk scoring based on detection confidence, method, and user behavior, significantly reducing false positives while maintaining high detection rates.
Detect Privacy Tools With IPinfo
Fraudsters will always look for ways to hide. VPNs and other privacy tools make that easier, but IPinfo also makes it easier than ever to identify them. By investing in strong privacy detection, businesses can understand user behavior more clearly and reduce their risk of fraud.
Whether you're protecting user accounts, digital assets, or ad spend, VPN detection should be a key part of your fraud prevention toolkit.
Get access to industry-leading IP data
Locate users, customize experiences, eliminate site risks, and much more.
About the author

Meghan is the content strategist at IPinfo, where she develops and writes content for users to better understand the value of IP data and IPinfo products.