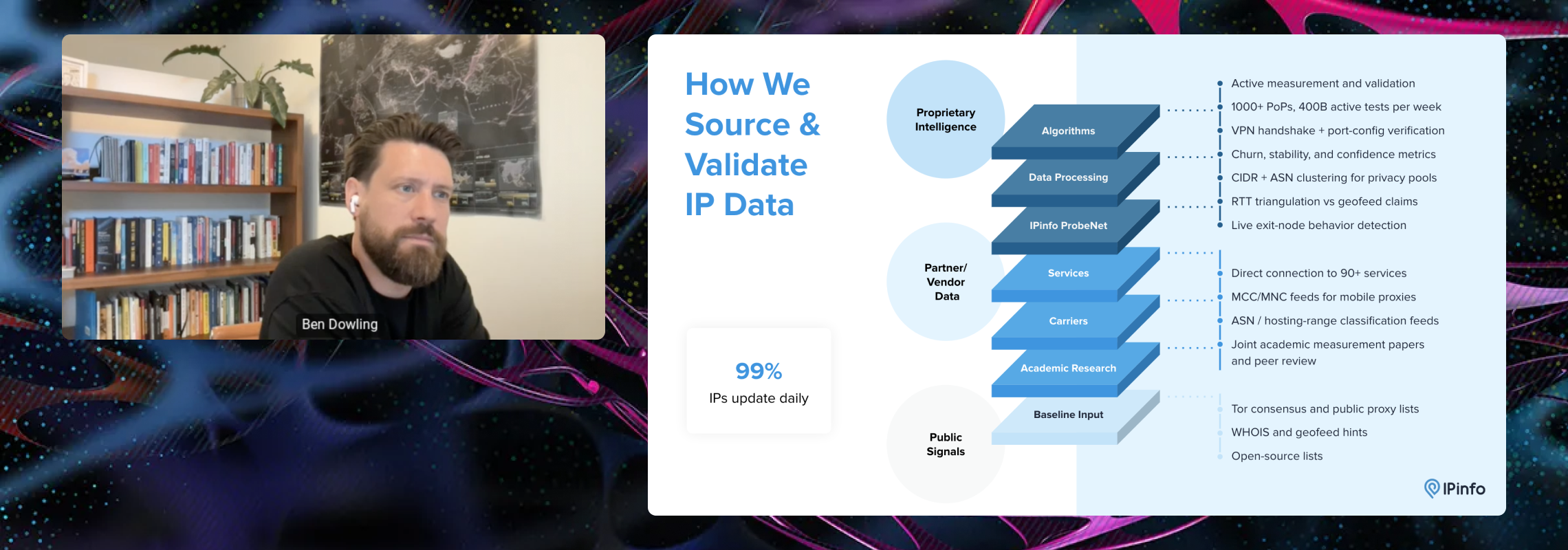
If you work in fraud prevention, security, or compliance, you know that IP addresses can offer critical signals — but interpreting those signals isn’t always straightforward.
In our recent Black Hat-hosted webinar, Co-CEO Ben Dowling walked through how anonymization tools like VPNs, proxies, and hosting relays show up in IP data, and what to watch for when trying to detect them. If you missed the live session, you can now watch the full recording below.
Key Takeaways
1. VPNs and proxies aren’t inherently bad.
Ben broke down how commercial VPNs, residential proxies, and hosting relays operate. Each behaves differently in IP-level signals, and each comes with its own risks, legitimacy, and detection nuances. Learn more about types of IP anonymization.
2. Raw IP signals need context.
An IP alone won’t tell you everything. But layered indicators can help build a much clearer picture. Ben shared examples of what constitutes strong evidence, and where common detection methods fall short.
3. There’s no universal threshold for “anonymized.”
Use cases vary, and so should your detection thresholds. Whether you’re trying to block abuse, flag suspicious behavior, or simply enrich logs with more metadata, understanding your tolerance for false positives is key. Ben talked through how to tune your approach depending on risk appetite and business logic.
4. Residential proxies are the hardest to catch.
These often mimic legitimate home traffic, making them harder to detect than VPNs. Ben shared techniques IPinfo uses to identify residential proxy networks at scale, including behavioral analysis and active probing. Find out what we've learned from tracking residential proxy data.
5. Anonymized IP detection fits into your stack, fast.
IPinfo integrates easily with your existing tools and workflows. Whether you’re enriching traffic in a SIEM or feeding real-time signals into a fraud engine, our APIs are built for performance and flexibility.
As Ben responded in the webinar, Splunk can flag anonymous VPN IP addresses with IPinfo data. We also offer native integrations for Google Cloud, Snowflake, Microsoft Security Copilot, Maltego, and more.
Our Approach at IPinfo
At IPinfo, labeling IPs as “VPN” or “proxy” is just the beginning. We verify anonymization signals daily and share nuanced service metadata via our Privacy Detection API. Our goal is to give teams better context so you can make more confident, accurate decisions. (Here’s how we recommend evaluating IP data accuracy.)
If you care about VPN and other IP anonymization data, check out the full webinar. Whether you're building fraud models, tuning security filters, or trying to separate legitimate users from anonymized traffic, the session is full of real-world insights you can put to work.
Reach out to us if you’d like to learn more about how we help teams detect anonymized traffic at scale.
About the author

Meghan is the content strategist at IPinfo, where she develops and writes content for users to better understand the value of IP data and IPinfo products.