In today's digital landscape, cybersecurity has become a critical concern for businesses and organizations. Cyber threats are constantly evolving, and cybercriminals are always looking for new ways to exploit vulnerabilities in infrastructure and networks.
In this context, IP address data plays a crucial role in the work of cybersecurity teams, including SOC as a service and security information and event management (SIEM). Here are several ways IPinfo’s cybersecurity users implement IP address data.
Attack Surface Management
Many well-known cybersecurity teams and organizations use IPinfo’s data to conduct attack surface management, including NetSPI, and Graylog. These and many other organizations conduct risk assessments and manage vulnerabilities by using IP address data to map their clients' or their organization’s assets.
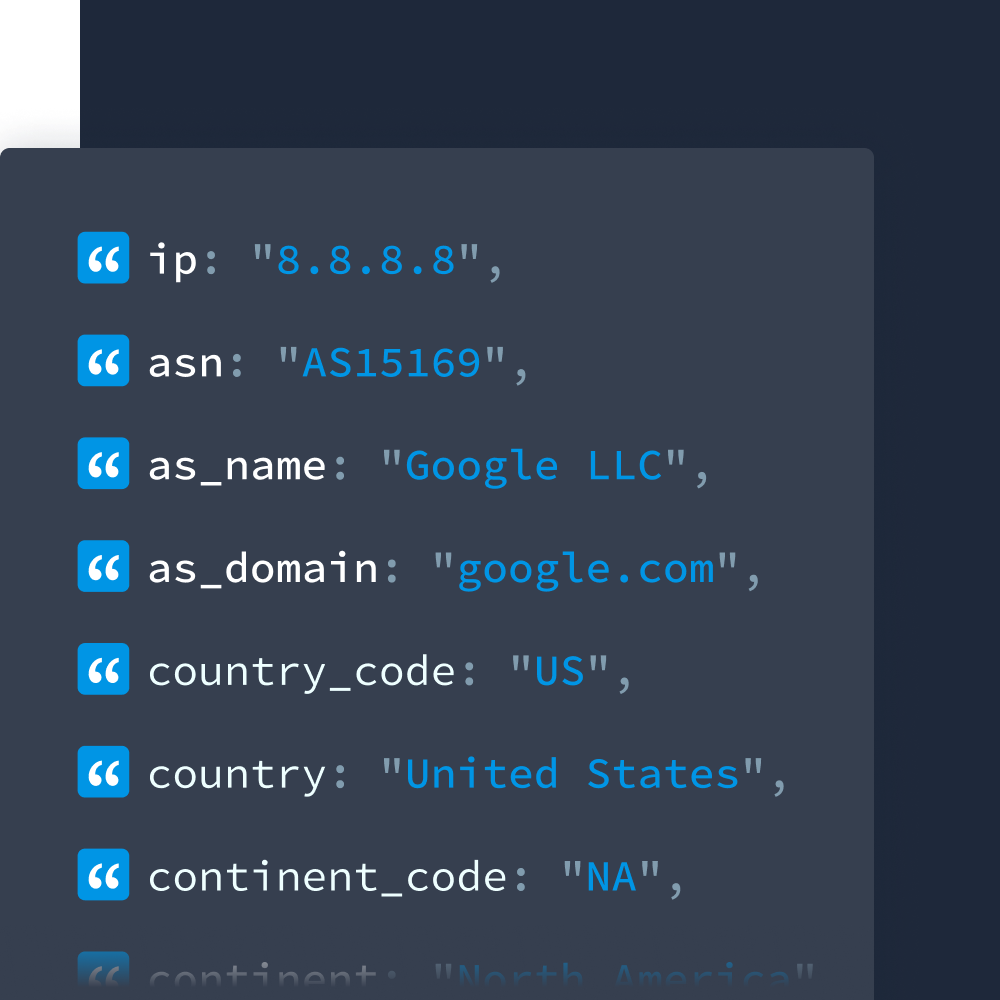
IP address data is an integral part of identifying systems at risk or vulnerabilities within networks. For organizations looking for threat actors, IP to Company is an important part of investigating IP ownership by companies. This particular dataset reveals the company name, domain name, network, and company type, such as business, hosting providers, ISPs, or educational institutions.
Using IPinfo’s data to determine what IP ranges are associated with companies is critical for attack surface management and network monitoring. Many security teams use our IP Ranges data to investigate ranges operated by a single entity.
Security teams also need to gather inferences from Hosted Domains data. These IP to Hosted Domains database download show a full list of domains that are hosted on a single IP address. This dataset can be used to investigate entry points such as landing pages and domains as part of the attack surface.
Security companies or teams also download the IP Whois database. With point of contact (POC), organization identifiers (ORG), and networks (NET) information, security teams can identify trends such as changes in IP address ownership, who owns the IP address, the organization ID, and much more.
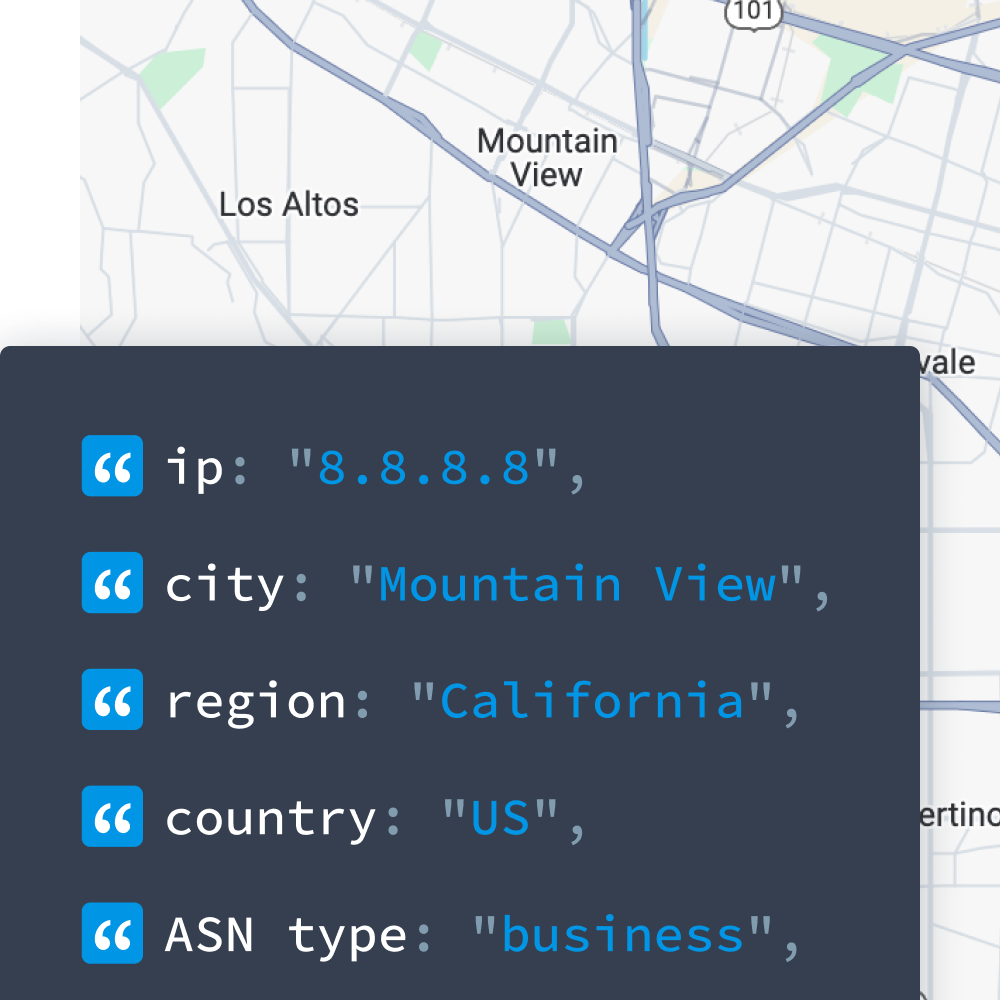
IP to geolocation data is another useful tool for cybersecurity teams who need to identify organizations that have different locations or franchises and who host a variety of networks that may or may not be connected.
Instantly Access Geolocation Data
IPinfo’s IP geolocation database delivers pinpoint accuracy, tailored to fit your unique business needs.
For some cybersecurity organizations, including cyber insurance, the impact of these datasets can reach tens of millions of dollars when vulnerable and targeted technology or network exposures are identified.
But without accurate IP address data, false alerts and faulty data inferences can result in more revenue losses. That’s why accurate IP address data plays a major role in mapping those attack surfaces.
Threat Actor Intelligence
Beyond monitoring a company's or customer's assets, many cybersecurity teams also use IP address data to map and investigate adversarial infrastructure and networks. Since threat actors continuously change their infrastructure over months, weeks, and sometimes days, network monitoring solutions often need IP address data that are updated daily.
That’s why many security organizations choose IPinfo’s data. These IP datasets are more than what users could aggregate from publicly-available IP address data. We’ve developed our own proprietary algorithms to monitor data accuracy, and our data engineers continually verify and improve our databases.
We also invest in ProbeNet, our internet measurement platform, which consists of more than 1,000 points of presence deployed worldwide, to verify IP address geolocation. In short, this data is accurate enough to keep pace with the accelerated investigations and intelligence needed by cybersecurity teams.
Cybersecurity teams specializing in threat actor intelligence focus on gathering as much information about adversary assets as possible. And they may still map out a company’s assets, but the focus of their investigations is quite different.
The implications of adversary threat intelligence are that when security teams notice communication between threat actors and the company’s network they’re monitoring, they can often infer that an attack is happening and often infer what type of attack is taking place.
Start With IPinfo Lite - Free Country & ASN Data
Get enterprise-grade IP intelligence with unlimited API calls, daily updates, and commercial use rights—no strings attached.
Managed Detection and Response
Managed detection and response (MDR) and security information and event management (SIEM) enrich traffic logs with IP address data for better outcomes and customer confidence. MDR relies on IP data to improve alerts based on anomalies detected in IPs accessing networks or systems. Enterprise customers like Panther, Datadog, Expel, Greylog, Arctic Wolf, and SentinelOne use IPinfo's data to fuel better MDR solutions, achieving dramatic improvements in threat detection speed and accuracy.
For companies like Wirespeed, IPinfo's data has enabled them to achieve a "1-Second Mean Time to Verdict (MTTV)" – reducing what traditionally took hours down to milliseconds. In one notable case, they detected a Russian hacker attempting to transfer money by identifying suspicious login activity – the user appeared to be logging in from Kentucky, but the abuse contact was based in Shanghai – and stopped the attack within 90 seconds.
“As a cloud-native SIEM that provides highly-scalable, real-time threat detection, Panther needs effective enrichment to make sure customers get the context they need fast. As a fellow Snowflake partner, IPInfo was an ideal choice for seamless alert enrichment - quickly adding the geolocation and ASN context our customers need to tune detections and accelerate triage.”
- Joren McReynolds, SVP of Engineering, Product & Design
Privacy Detection is an important data source for MDR because it returns masked IPs, including VPNs, proxies, tor usage, relay usage, or connections via a hosting provider. Any of these could potentially be used to tunnel traffic into networks by hiding the true location of the user.
Our comprehensive Privacy Detection capabilities include:
- VPN detection (with specific service provider names)
- Proxy identification
- Tor exit nodes
- Relay services
- Hosting providers
- Residential proxies
The new Residential Proxy Dataset specifically targets IPs being used to route traffic through legitimate residential networks, which are particularly challenging to detect with traditional methods. This dataset provides metrics like percent_days_seen and last_seen to help identify these transient proxies and distinguish between legitimate and suspicious anonymized connections with greater precision..
IP to Geolocation also helps SIEMs enrich traffic logs with relevant geolocation information from around the world. This dataset includes hostnames, location coordinates to the nearest city center, region, postal or zip code, country, and city-level insights. SIEMs use geolocation data to detect higher-risk alerts.
Along with these other datasets, IP to Company and ASN data are important for enriching alerts and gathering further context. This dataset reveals the country, number of IPs, allocation date, hosting, registry, and hosting service of an IP address. Enterprise organizations use these insights to detect suspicious connections between data centers or IPs known for malicious activity.
In addition to datasets, organizations like Panther use IPinfo’s integrations to seamlessly implement IP address data into their workflow and log enrichment. This is why IPinfo offers supported integrations like Snowflake, Google Cloud Platform, Splunk, and Palo Alto.
Eliminating Alert Fatigue
One of the biggest challenges for security teams is alert fatigue – the flood of false positives that wastes analyst time, delays real threat detection, and erodes trust in security automation. Poor-quality IP intelligence is often the culprit.
IPinfo's precise geolocation and privacy detection data helps security teams:
- Drastically reduce false positives with high-confidence geolocation data
- Accurately identify impossible travel scenarios by distinguishing between genuine geographic anomalies and routine VPN usage
- Free security analysts to focus on critical incidents rather than manually verifying questionable alerts
- Build reliable security automation that security teams can trust
As Jake Reynolds, Co-Founder/CTO at Wirespeed explains:
"We work with all the leading security providers, but the location data they include is often so inaccurate that we couldn't automate effectively. IPinfo solved a major accuracy gap and made impossible travel events and other automated threat detection truly viable."
Fraud Prevention
Organizations also use IP address data to prevent fraud. IP address data is a useful part of automated fraud scoring models and helps a variety of companies, from cybersecurity to financial institutions, establish better fraud detection. Several of these include Feedzai, Forter, Nethone, Dupaco, and Adcash.

IP to Geolocation data is used to detect the origin of transactions. Dupaco, a financial institution, uses this dataset specifically for this purpose. If a transaction occurs in a location that’s inconsistent with the account holder’s location, this transaction will trigger an automatic alert for security teams.
Just as important as locating the origin of a transaction is determining if traffic is hiding its true location. According to Nethone, an organization that uses IPinfo’s Privacy Detection data to develop bleeding-edge fraud detection software, “Almost every single fraud method involves some form of VPN. It’s a crucial parameter to detect when someone is about to commit a crime.”
Our latest Privacy Detection Extended dataset provides deeper insights into anonymization methods with additional technical attributes that reveal exactly how we detected each IP address, including:
- Confidence levels (1-3) indicating certainty about the privacy service detection
- First_seen and last_seen dates tracking when activity was first and most recently observed
- Coverage percentage for inferred ranges showing what proportion has direct evidence
- Detection method indicators including census, device_activity, VPN_config, and WHOIS
IP to Company API and database downloads are also used in fraud scoring. This is because IP to Company returns the type of organization behind an IP address. For instance, if an IP address belonging to a hosting provider (as opposed to a residential user) tries to access a private bank account, this transaction can be flagged as suspicious and investigated further.
All this to say, many organizations leverage IPinfo’s accurate IP data to develop reliable fraud prevention use cases.
Security Operations Centers
Security operations centers (SOCs) require a team of experts to monitor security operations within an organization. For some organizations, this is too costly due to staffing, licenses, hardware, and many other expenses. SOC as a Service (SOCaaS) teams offer a reliable and affordable third-party alternative for organizations who aren’t ready to fully service an in-house SOC.
IP address data is important for SOC and SOCaaS (Security Operations Center as a Service) because they need to reliably identify malicious traffic for their users. False positives and false negatives slow down their internal processes and reduce confidence among customers.
For instance, even if SOCaaS providers’ alerts are accurate one-hundred times, customers seem to remember the one time that inaccurate IP data triggers false alerts. Again, this is why these security organizations choose IP address data providers who update and improve their IP data every day.
Automation is an important facet for SOC and SOCaaS, and IP address data helps contextualize threats and identify them as high-risk or not.
Is this data accurate enough to build reliable threat intelligence?
SOC teams monitor login attempts and investigate suspicious events within other organizations. Data such as IP to Geolocation, Privacy Detection, IP to Company, ASN data, and IP Whois data help SOCaaS teams determine the highest risks and develop automated systems to monitor, protect, respond, and remediate attacks in a timely fashion for their customers.
Many of these organizations find that IP data as a service is highly valuable for their team. IPinfo allows these teams to spend more time focusing on alerts and customer needs rather than collecting and validating IP address data.
IP Address Data You Can Trust
In short, IPinfo provides cybersecurity teams with high-quality IP intelligence that would be impossible to replicate internally. Recognized as the benchmark for IP data accuracy, IPinfo delivers enterprise-grade reliability processing billions of daily requests with zero downtime – no forced maintenance windows or disruptions that plague other providers.
Building comparable datasets would require a global infrastructure of hundreds of probe servers, complex data processing pipelines, and dedicated teams of data scientists and engineers – investments far beyond what's feasible for most organizations. Many security providers report they can fully integrate IPinfo "in minutes" with a simple API that just works.
By choosing IPinfo as their IP data provider, cybersecurity teams can focus on their core mission while leveraging data infrastructure and expertise that has taken over a decade to develop. And with continuously evolving datasets like Residential Proxy detection, IPinfo ensures security teams stay ahead of emerging threats and new evasion techniques.
Why IPinfo?
- All the IP data (less of the headache): We process over 20 terabytes of data while maintaining 99.99% uptime. With our wide variety of datasets, IPinfo provides all the IP insights you'll need in one place.
- Comprehensive data validation: Through our ProbeNet of 1,000+ points of presence deployed worldwide and our advanced data processing methodology, we achieve industry-leading accuracy.
- Daily updates: IP address data changes regularly—8% of city-level IP data changes weekly, 16% changes monthly, and 44% changes yearly. Our data is refreshed daily to ensure you have the most current information.
Plus, IPinfo is a one-stop IP address data source. We offer 10+ contextualized datasets that can be accessed the way you choose, via APIs or data downloads. IPinfo invests heavily in accurate data with in-house data engineers, proprietary algorithms, and robust traceroute systems so that our cybersecurity users have IP data they can trust.
Get instant access to industry-leading IP data
Locate users, customize experiences, eliminate site risks, and much more.
About the author

As the product marketing manager, Fernanda helps customers better understand how IPinfo products can serve their needs.