Get Unlimited Access to IPinfo Lite
Start using accurate IP data for cybersecurity, compliance, and personalization—no limits, no cost.
Sign up for freeAs internet privacy tools become more popular, VPNs have quickly moved from niche tech to everyday browsing tools. More than 40% of internet users have used a VPN.
For consumers, VPNs promise anonymity and access to geo-blocked content. But for a wide range of companies, VPN traffic can pose a serious challenge. VPN usage makes user verification, regional targeting, and threat detection more complicated. That’s why VPN detection is no longer optional – it's critical infrastructure for any company dealing with IP data.
In this guide, we’ll explore how VPNs affect IP visibility, why detecting them matters, and how IPinfo’s VPN detection uses real-time protocol scanning, behavioral anomaly analysis, and IP reputation tracking to spot VPN traffic with unmatched precision.
How VPNs Affect IP Visibility
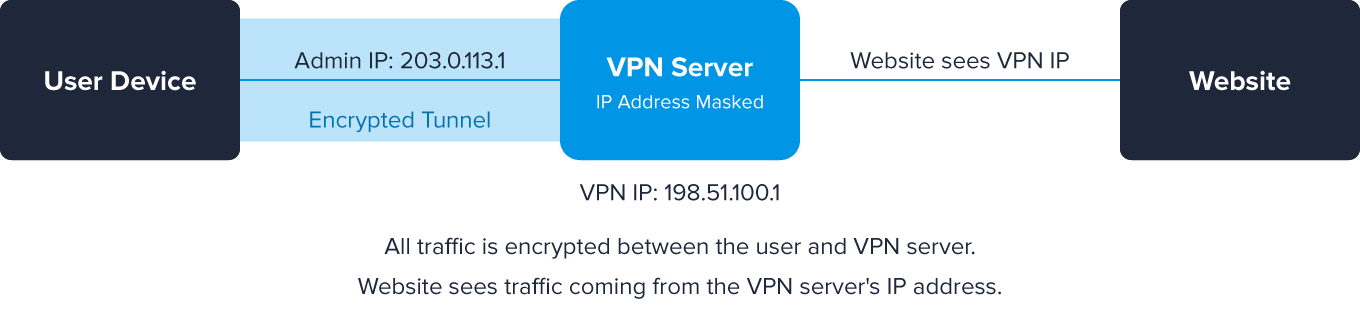
When a user connects through a VPN, their real IP address is masked, replaced by the IP of the VPN server and obscuring their identity.
This redirection creates several challenges for businesses that rely on accurate IP data:
The Technical Details
- Connection Rerouting: Without a VPN, a user's connection travels directly from their device to the destination server, clearly revealing their true IP address. With a VPN activated, the connection is first encrypted and then routed through an intermediary server – often in a completely different geographic location.
- Encrypted Tunneling: VPNs create an encrypted tunnel between the user and the VPN server. All traffic inside this tunnel is protected from outside inspection, making it impossible to see the user's original information without access to the VPN provider's logs.
- IP Substitution: The destination website or service only sees the VPN server's IP address, not the user's actual address. This substitution affects all IP-dependent systems and decisions.
Business Impact
- Location Misrepresentation: A user physically located in Tokyo might appear to be browsing from Amsterdam, Toronto, or São Paulo depending on their VPN server choice. This undermines location-based services, content restrictions, and regulatory compliance measures.
- Identity Obfuscation: VPNs break the connection between a user's digital activity and their physical identity, complicating user tracking, behavior analysis, and fraud detection efforts.
- Shared IP Addresses: Commercial VPNs often have thousands of users sharing a single IP address simultaneously. This makes it nearly impossible to isolate individual user activity using traditional IP-based identification.
- Dynamic IP Rotation: Advanced VPN services implement automatic IP rotation, changing the user's apparent IP address at regular intervals or with each new connection, further complicating tracking and identification.
The Scale of the Challenge
The VPN landscape continues to evolve, with providers constantly adding new servers and IP ranges to their networks. Major commercial VPNs like NordVPN and ExpressVPN maintain thousands of servers across hundreds of locations, while smaller providers emerge regularly.
This dynamic environment means that static IP lists quickly become outdated, requiring sophisticated detection techniques that can adapt to this ever-changing ecosystem.
Understanding these mechanisms is crucial for developing effective strategies to identify VPN traffic and make appropriate business decisions based on this knowledge.
Experience best-in-class IP privacy data
With IPinfo, discovering IP addresses using anonymization tools is easier than ever.
Why VPN Detection Matters
Whether you're fighting fraud or optimizing content delivery, knowing when an IP is associated with a VPN helps you make better decisions. Here’s how:
Cybersecurity and Fraud Prevention
VPNs are often used to obscure malicious behavior – everything from credential stuffing and account takeovers to DDoS attacks. For fraud teams, detecting VPN usage adds an important signal to risk scoring. It helps identify suspicious logins, prevent fake account creation, and stop fraud rings that rely on anonymized traffic to evade detection.
Compliance With Digital and Regional Regulations
For industries bound by content licensing agreements or regional regulations, enforcing regional access controls is non-negotiable. VPNs can be used to bypass these controls, exposing companies to compliance risks. VPN detection helps ensure that only users from approved geographies can access regulated services.
Ecommerce
In ecommerce, VPN usage can distort pricing models, geolocation-based discounts, and tax calculations. It can also mask bots scraping product data or performing inventory hoarding. Detecting VPNs allows retailers to maintain fair pricing strategies, prevent abuse, and deliver accurate customer experiences.
Fintech
Trust is everything in financial services. VPNs can signal account access from unusual or high-risk environments, which might indicate fraudulent intent or policy evasion. VPN detection plays a crucial role in transaction monitoring, identity verification, and fraud prevention workflows across banking, trading, and crypto platforms.
Gametech
In gaming, VPNs are often used to spoof regions for early access, exploit matchmaking systems, or bypass regional bans. This undermines game balance and can affect player safety. VPN detection helps enforce fair play, protect geo-locked content, and uphold community standards.
Adtech
Advertisers depend on accurate IP data for targeting, analytics, and attribution. VPN traffic can distort location signals, inflate impressions, and lead to ad fraud. By identifying VPNs, adtech platforms can refine audience segments, filter invalid traffic, and improve ROI for their partners.
How VPN Detection Works
Effective VPN detection starts with accurate IP data. 10% of privacy IP data changes monthly, making fresh data critical. However, most IP data providers rely on static lists of known VPN servers, supplemented with basic Whois data, making their data less reliable.
IPinfo combines static identification with dynamic detection and active verification methods, enabling superior IP data accuracy. Our process includes:
- Active protocol detection: We scan for VPN and proxy protocols across the entire IPv4 space
- Behavioral analysis: We identify anomalous routing patterns and connection behaviors
- Temporal tracking: We monitor how IPs move in and out of privacy services over time
- Service correlation: We map relationships between IPs and specific anonymization services
VPN Detection with IPinfo
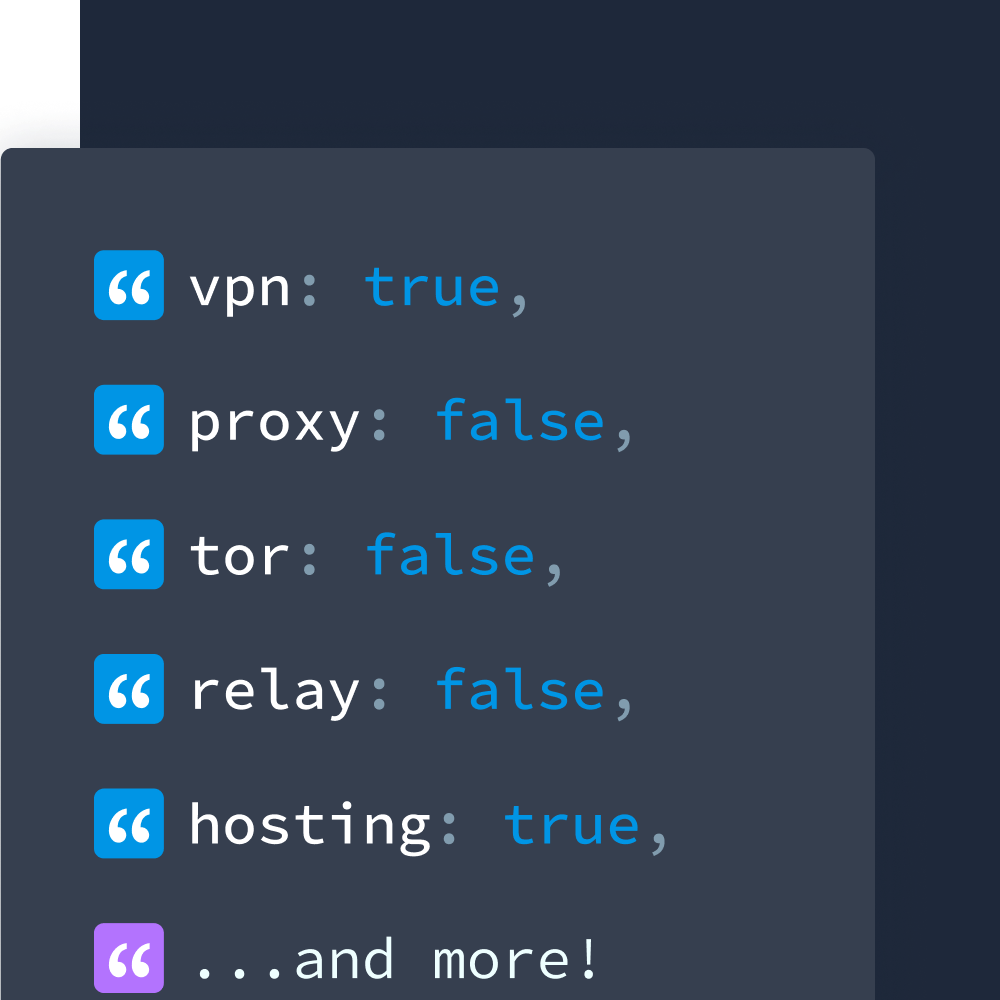
Our Privacy Detection data lets you detect not only whether an IP address is associated with a VPN, but also:
- Service provider identification: Names of specific VPN services
- Confidence scores: Certainty levels for each detection (1-3)
- First/last seen dates: Historical tracking of when IPs entered or left privacy services
- Detection methods: Transparency about how each IP was identified
This granular data allows teams to make nuanced decisions – whether it’s tightening access controls, adjusting fraud risk scoring, or delivering personalized content.
While many providers rely on outdated blocklists or simple Whois lookups, IPinfo's active scanning and behavior-driven model ensures that our privacy data is updated in real time – capturing emerging VPN servers and proxy IPs faster and more accurately.
Flexible Solutions for Every Detection Need
IPinfo offers a comprehensive suite of privacy detection solutions designed to match your specific business requirements, technical capabilities, and budget constraints:
- Basic Privacy Detection: IPinfo Core provides essential anonymous IP identification through straightforward boolean flags. This entry-level solution helps you quickly determine if an IP address is associated with VPN, proxy, Tor, or relay providers.
- Privacy Detection with Specific Service Identification: For deeper context, our IPinfo Plus detection package includes identification of specific service providers and the anonymization technology used, helping security teams develop more sophisticated risk models and fraud prevention strategies tailored to specific privacy services.
- Advanced Privacy Detection: Our most comprehensive solution is the Privacy Detection Extended Database, providing full transparency into our detection methodology with detailed technical attributes that reveal exactly how each IP was identified. This enterprise-grade solution is ideal for organizations where understanding the specific detection methodology is critical for decision confidence.
Implementation Flexibility
Our privacy detection solutions are available through real-time REST API for dynamic application integration and downloadable databases for local deployment and offline processing. We also offer cloud provider integrations with Snowflake and GCP and custom data delivery pipelines tailored to your infrastructure.
Whether you're building a customer-facing application, enhancing internal security systems, or developing a hybrid approach, IPinfo's flexible delivery options ensure you can implement privacy detection precisely where and how you need it.
To learn more about identifying anonymous IPs, download our ebook “The Essential Guide to Anonymous IPs and Privacy Detection Data.”
Get Started With IPinfo
VPNs are here to stay. While they empower users to browse more privately, they also raise the bar for companies that rely on accurate IP data. VPN detection bridges that gap – keeping user experiences smooth and secure, while giving teams the insights they need to protect their systems and reputations and deliver with precision.
Whether you're building a fraud detection engine, serving location-specific content, or defending against abuse, having trusted IP data is your best defense.
See VPN detection in action
Get started with IPinfo’s Privacy Detection API today to prevent fraud and save money.
About the author

Meghan is the content strategist at IPinfo, where she develops and writes content for users to better understand the value of IP data and IPinfo products.