Two weekends ago a large gaming platform watched 1,200 “new” accounts appear in barely two hours, each from a different U.S. residential IP. Every velocity check, block list, and geo rule said low risk, so the accounts sailed through, exploited a promotional offer through synthetic signups, and vanished. Ten days later, $60k in chargebacks hit. When the team replayed the traffic against IPinfo’s Residential Proxy data, every single IP matched active residential proxy signatures in our dataset.
That story isn’t an edge case. Residential proxies are now the fraudster’s next hop after VPNs and hosting addresses: they rotate quickly, look like real home or mobile users, and evade static detection mechanisms and allowlist policies.
That’s why we built the IPinfo Residential Proxy API. We’ve long offered this data as downloadable files and via Snowflake. But after months of requests from customers, we’re launching what one fraud team called their “missing weapon”: instant API access to residential proxy intelligence.
It delivers intelligence provider name, persistence score, and mobile-gateway flags so you can check/validate logins, protect bonus budgets, and shut down fraud before the money (or the promo credits) leaves your wallet.
Residential Proxy Detection Snapshot
In the last 90 days alone, IPinfo has tracked 47 million unique residential-proxy IPs across 85 networks. To see how fast those addresses churn, I compared two daily snapshots. Between the two days, roughly 2.2 percent of the IP addresses appeared or disappeared in just 72 hours.
Some networks dropped half their IPs over a weekend. Others added a third of their supply as never-before-seen addresses. Mobile proxies were even more unstable, with nearly 3% disappearing and 2.4% newly appearing in just 72 hours.
These are rough snapshot figures, but the trend is clear: static blocklists are too slow for an ecosystem this dynamic. If you're relying on yesterday’s IPs, you’re already missing today’s threats.
We'll be diving deeper into residential proxy patterns and other IP intelligence insights in upcoming posts.
A Critical Detection Layer for Your Privacy Stack
Sophisticated threats usually follow a predictable escalation: when your defenses block VPNs and data center traffic, attackers pivot to residential proxies to bypass checks, evade geo-restrictions, and blend into legitimate user patterns.
The Residential Proxy IP data adds a critical detection layer that standard Privacy datasets miss. While our existing Privacy datasets flag VPNs, data center proxies, and Tor traffic, residential proxies route through legitimate home and mobile devices requiring specialized methods to detect them.
With low-latency responses (<200 ms), 99.9%+ uptime, and daily refreshed data, it gives your systems the ability to:
- Score sessions during onboarding or login
- Enrich investigations without delaying response
- Surface volatile residential traffic before it’s too late
Worried your detection system missed something? Run recent traffic against our Residential Proxy dataset — and see what your current stack isn’t catching. Learn more.
Actionable Intelligence Beyond a Binary Flag
Most residential proxy detection solutions stop at a binary flag. We provide context across three key dimensions:
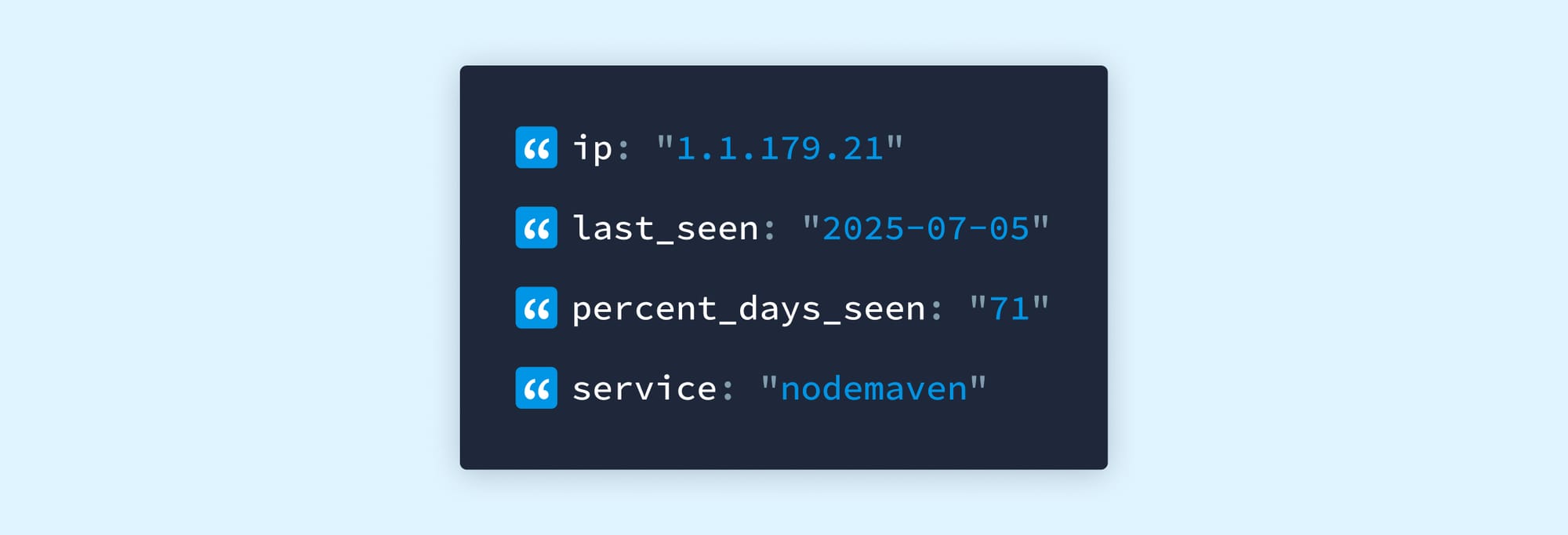
- Temporal Context: Time-stamped last seen proxy activity and rotation frequency that doubles as a risk indicator. Here, “percent_days_seen: 71” means this IP was active as a residential proxy 71% of days in the last 7 days, a high-risk indicator.
- Provider Intelligence: Know exactly which residential proxy provider the IP is associated with.
- Mobile Gateway Detection: Because mobile gateways are a growing part of the abuse surface, we tag those with the _mobile suffix on the service name (e.g., soax_mobile).
Choose Your Deployment
We offer multiple ways to access Residential Proxy IP data depending on your specific requirements:
- API (7-day window). Live scoring, incident response, and low-latency threat detection. Ideal for login flows, WAF integrations, and spike investigations: no infrastructure needed.
- Database Downloads (90-day window). Best for high-performance detection pipelines. Daily file drops ensure freshness without overloading your stack.
- Snowflake (90-day window). Designed for analysts and data teams. Use native SQL to join proxy intelligence with your internal datasets: perfect for model training, dashboarding, and retrospective investigations.
Some teams combine methods: loading files into detection pipelines, querying Snowflake for investigations, and using the API in parallel to get fresh context during time-sensitive flows. Integrates seamlessly with your existing stack including Splunk, and major SIEM platforms.
Where Residential Proxy IP Data Proves Critical
Most fraud and abuse systems already block VPNs and known hosting IPs. But once attackers move to residential proxies, the signals are harder to spot and the damage escalates fast.
We’ve seen this play out across a wide range of industries. A gaming platform lost $60k in welcome bonuses in just 48 hours before tracing the accounts to fast-rotating residential proxies. Their velocity controls flagged nothing: every IP looked like a clean, fresh consumer ISP.
A demand-side ad platform saw a 30% drop in invalid traffic (IVT) almost overnight after they began blocking residential proxy traffic. In another case, a SIEM vendor reduced false-positive alert noise by 35% in a single test run by enriching login events with proxy and privacy data — allowing their system to better distinguish real threats from benign traffic.
And it doesn’t stop there. Fintech teams use proxy intelligence to flag high-risk account signups tied to bonus abuse and synthetic identities. Travel platforms use it to detect scraping operations hiding behind residential IPs. Streaming platforms use residential proxy detection to catch geo-spoofing and block access to region-locked content. Ecommerce and SaaS platforms rely on it to prevent regional price arbitrage, fake account creation, and abuse of location-based discounts. Even limited-edition drops and ticketing systems now rely on proxy signals to keep scalper bots at bay.
From scoring logins to investigating threat spikes, residential proxy detection helps teams:
- Identify login attempts routed through rotating proxy infrastructure
- Distinguish legitimate user traffic from mass automation
- Add proxy intelligence to fraud, SOC, and threat triage tools
- Reduce alert fatigue with better risk scoring, fewer false-positives
If your privacy scoring stops at VPNs, our Residential Proxy dataset will add a layer that’s purpose-built for what gets through instead.
Ready to Explore Residential Proxy IP Data?
Residential proxies represent one of the most challenging detection gaps in modern threat environments. Their ability to impersonate real users at scale makes them a critical risk vector. IPinfo’s Residential Proxy Detection data provides the context and coverage needed to close this blind spot.
Whether you want to test, integrate, or just explore what’s possible, here’s how to dive in:
Read the API and Data Download documentation to see how the data is structured and how quickly you can start querying. Browse the dataset on Snowflake Marketplace if your team prefers native SQL access for joins, dashboards, or model training.
Ready to catch what your current stack misses? Get in touch and start detecting residential proxy traffic today.
About the author

As the product marketing manager, Fernanda helps customers better understand how IPinfo products can serve their needs.