My IP ↗or
My IP ↗orHow People Hide Their IPs and Why It Can Be Useful to Detect Them

The internet is built on the premise of open exchange of information, but that openness also comes with risks. People hide their IP addresses for many reasons – some for privacy and security, others for more questionable purposes. While privacy-conscious users may want to protect their personal data, cybercriminals exploit the same methods to mask fraudulent activities.
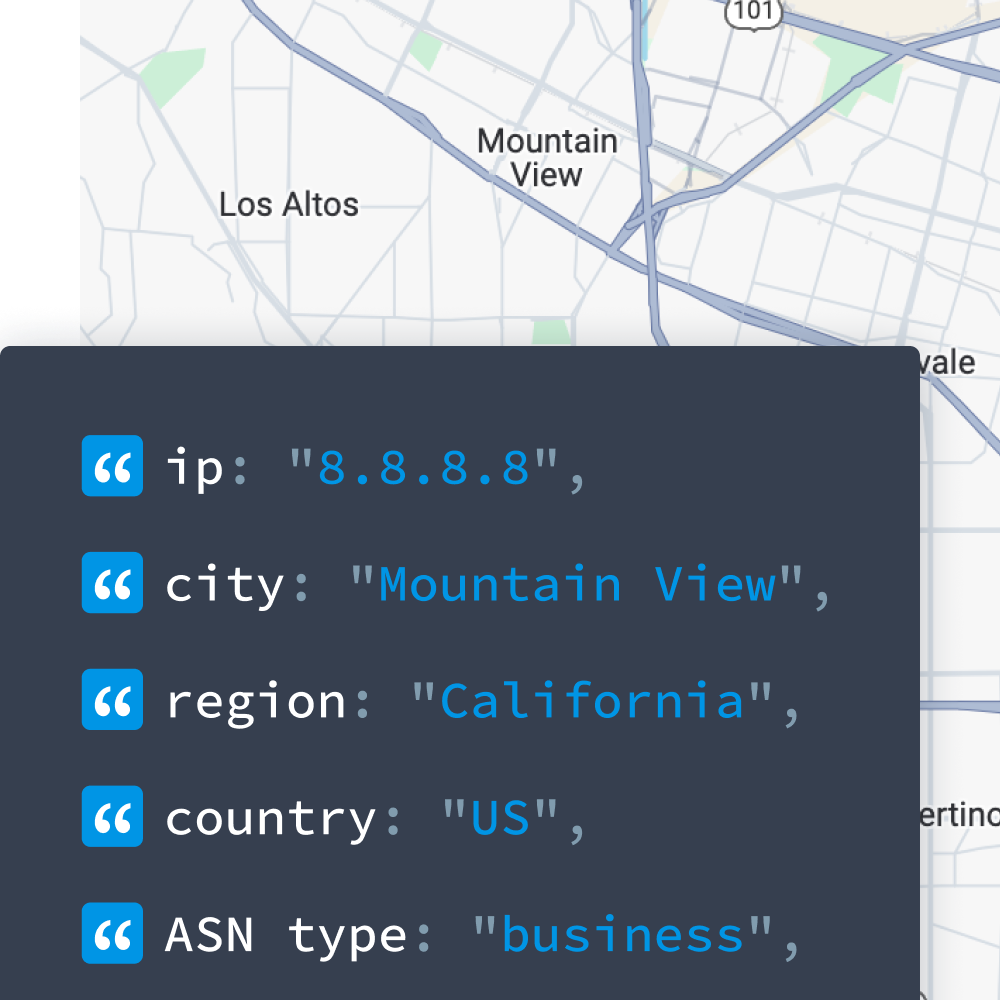
Every computer, router, or other device has an IP address assigned to it for sending and receiving internet data. That IP address has information attached to it, the way a physical address does, in order to communicate.
We are going to show you the various ways people hide their real IPs, why they do it, as well as why you need to detect them. We’ll also explore how IPInfo can help protect your company from bad actors.
Why Do People Hide Their IPs?
There are several reasons why people hide their IP addresses.
- Privacy Protection: Some users want to maintain their online privacy, keeping their browsing habits, locations, and personal data secret.
- Enhanced Security: Similarly, if they’re using an internet connection they don’t trust, an anonymous IP can keep their data safe from unauthorized data collection.
- Geographic Restrictions: Other users seek to access blocked content, whether for streaming services or due to censorship circumvention.
- Fraudulent Activities: Unfortunately, some users are cybercriminals who use anonymous IPs to make their efforts more difficult to detect.
In 2025, more than 40% of internet users have used tools like VPNs to mask their identities for various reasons. There are multiple ways to anonymize IPs.
How Do People Hide Their IPs?
There are six main ways that internet users hide their real IP addresses.
1. Hosting Providers
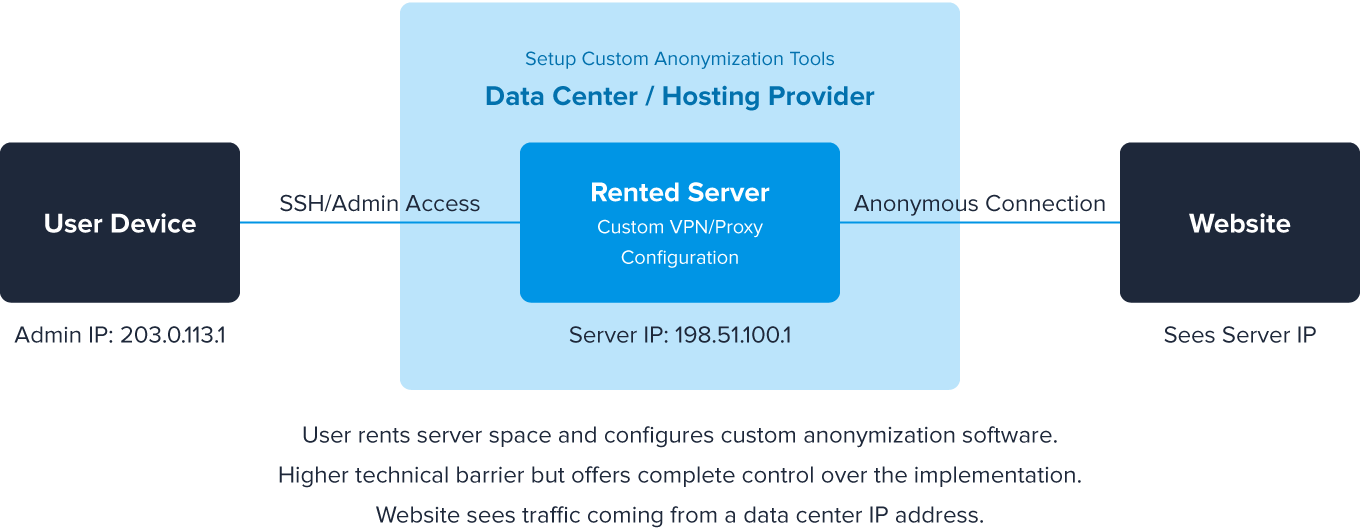
Hosting providers are a flexible anonymization option that allows users to customize their solutions. Providers offer servers in data centers that can be rented and configured, then fully controlled with whatever tools users select.
Because they’re static data center IP addresses associated with a hosting company, however, they’re easier to identify as non-residential traffic. They also require some technical knowledge to implement.
2. VPNs
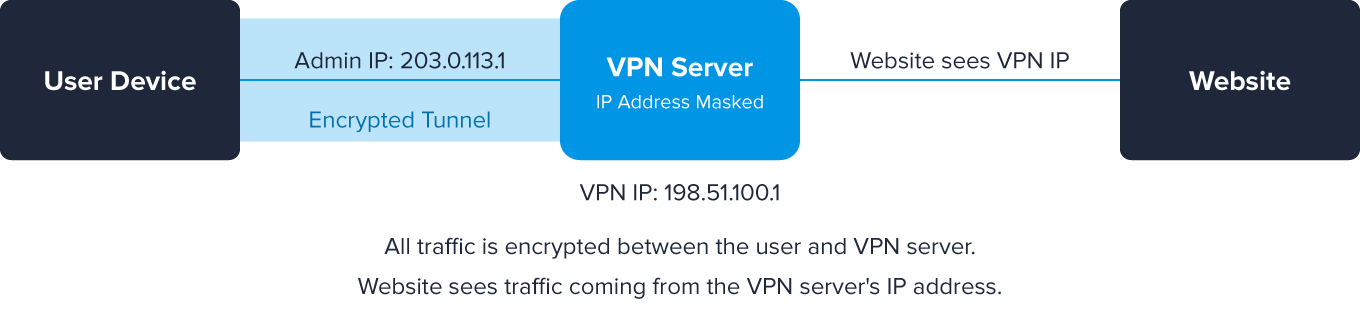
A VPN, or virtual private network, acts as a middleman between a computer and the destination server. It serves two purposes – one is to encrypt users’ connections to the internet and the other is to mask users’ original IP addresses.
To hide an IP address with a VPN, users just need to download a VPN (such as NordVPN or ExpressVPN), log in to it, and turn it on.
3. Proxies
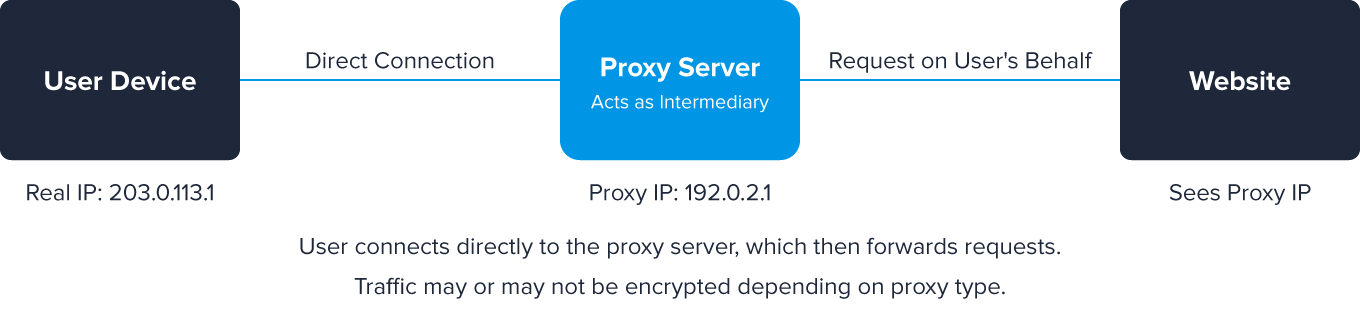
Another way users hide their IP addresses is by using proxy servers. In essence, what the proxy does is forward the client’s or network’s requests, acting as an intermediary, and receives and delivers server responses.
They may or may not encrypt traffic, which is why proxies tend to be less secure than VPN servers when it comes to online privacy.
Proxies generally fall into two categories:
- Datacenter proxies: Hosted in cloud providers or dedicated server farms with IP ranges easily identifiable as non-residential. These are more common but easier to detect and block.
- Residential proxies: Route traffic through regular consumer ISP connections, making them appear as legitimate residential users. These are more difficult to detect as they use IPs assigned to real households.
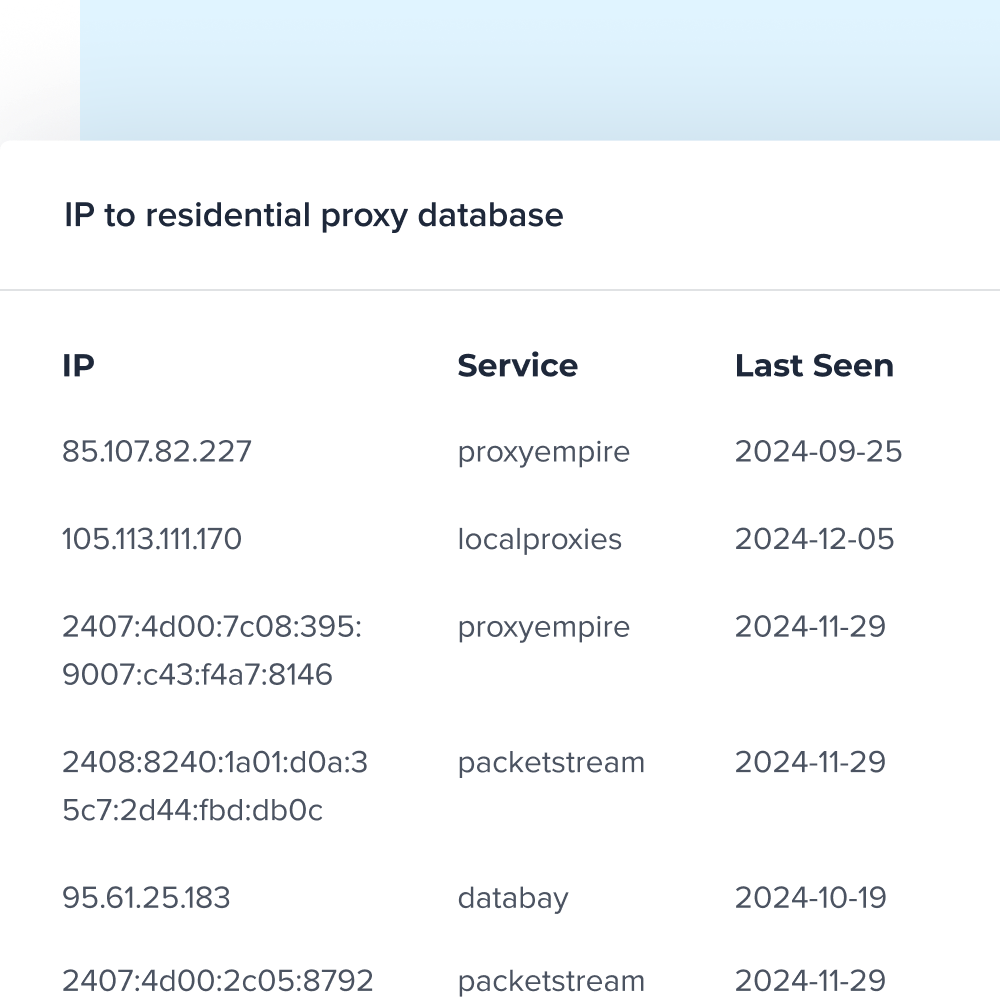
4. Residential Proxies
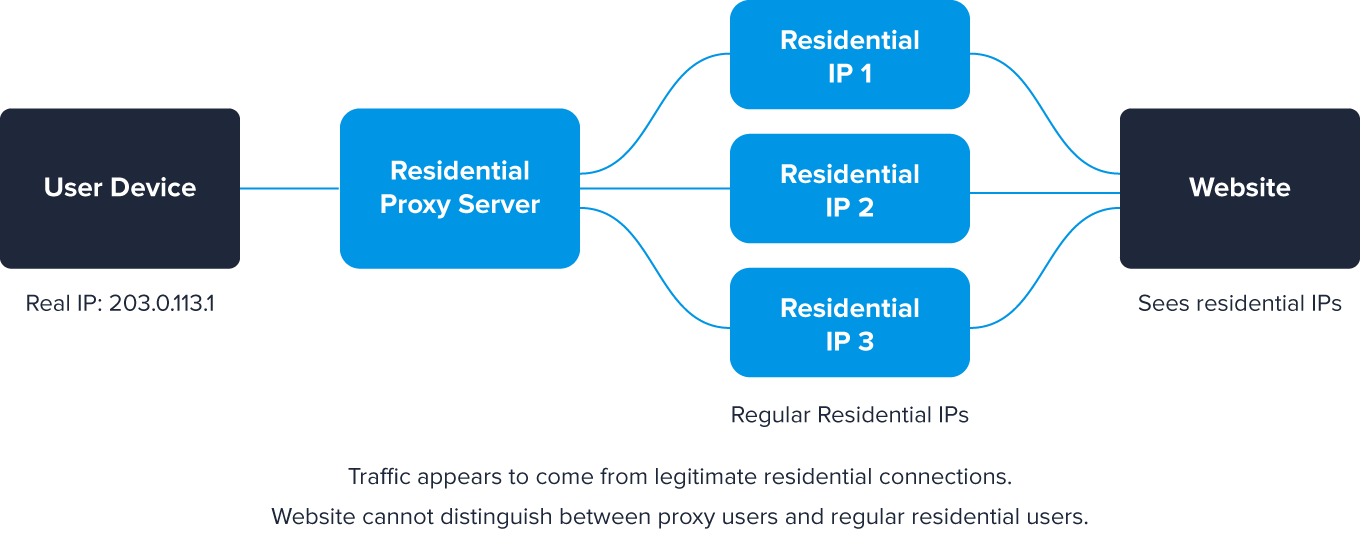
Residential proxies are becoming increasingly popular, routing traffic through regular home internet connections, making them appear more legitimate.
These networks are often created through questionable methods:
- Users unknowingly install software bundles or 'free' apps that include hidden proxy functionality in their terms of service
- Malware that converts everyday devices into proxy exit nodes without user awareness
- Compensation schemes offering small payments or free services in exchange for sharing bandwidth
- SDK integrations in legitimate apps that allow proxy functionality as a background process
This makes residential proxies particularly challenging to detect since the traffic comes from genuine residential IP addresses assigned by legitimate ISPs to real households.
Detect residential proxies with accurate IP data
Add a critical layer of defense to your fraud prevention and security workflows by identifying residential proxy IPs.
5. Relays
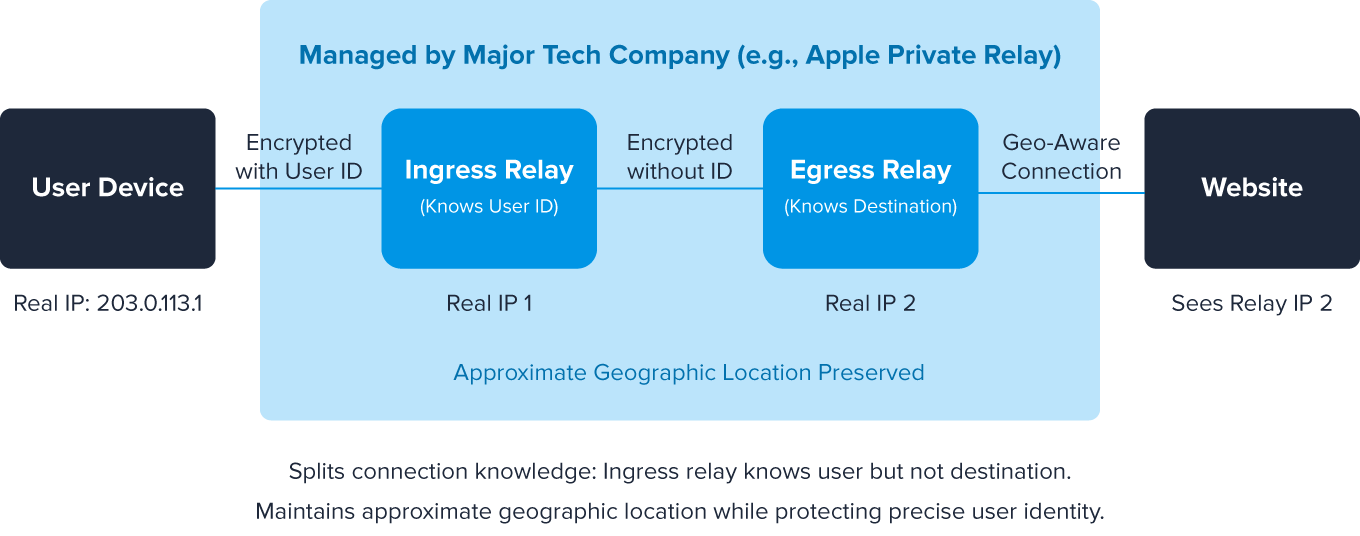
Relays work similarly to proxies, acting as intermediaries between users and websites. They’re typically operated by large tech companies (like Apple’s iCloud Private Relay). Modern relay systems use a dual-relay architecture:
- Ingress relays: The first server in the chain knows the user's identity but not their destination
- Egress relays: The second server knows the destination but cannot identify the original user
This split-knowledge approach preserves some geographic context while protecting privacy, so general location information remains intact (often at the city or region level) without revealing the precise user identity. This makes relays a compromise between complete anonymity and functionality.
6. Tors
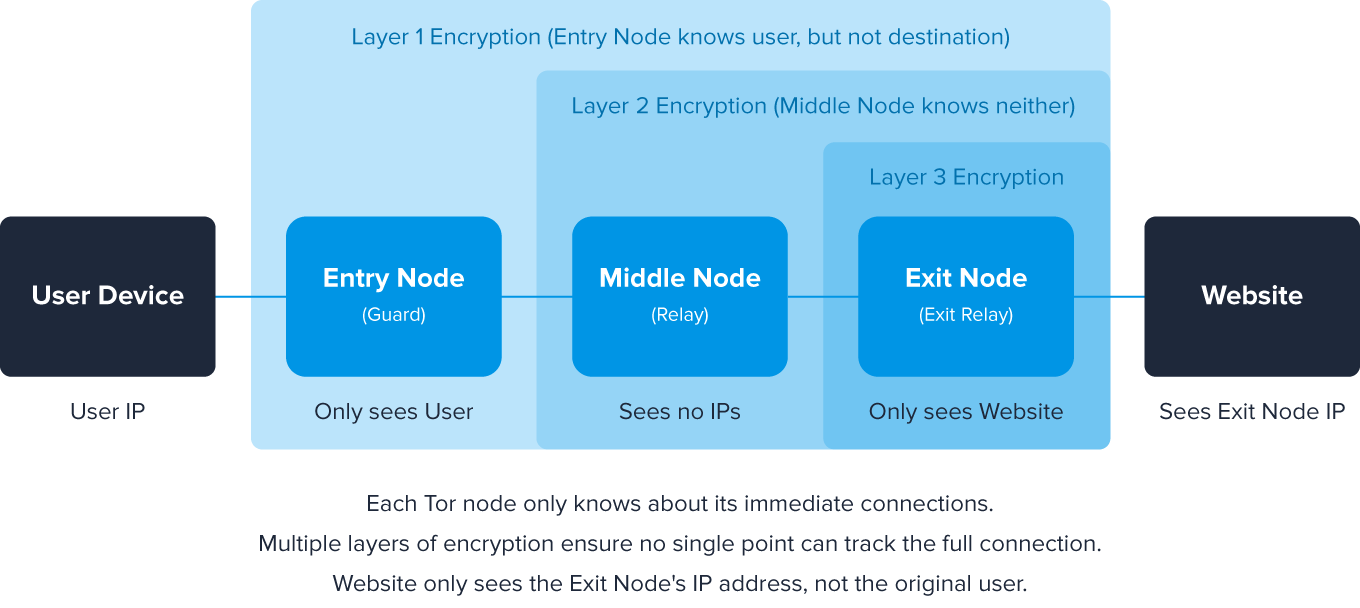
Tor, or The Onion Router, is an open-source and free network of server nodes run by volunteers that hides your identity behind layers of relays (like an onion, hence the name). The multiple relays only know the previous and next step in the route, so it’s difficult to trace.
This makes Tors excellent at hiding real IP addresses, but all that bouncing from node to node has its price – the traffic takes longer to complete the journey.
How to Detect If Your Visitors Are Using an IP Anonymizer
Although there are plenty of legitimate reasons why someone would want to hide their IP address, there are many that aren’t so legitimate. Identifying the latter is critical. So is getting it right.
Traditionally, privacy IP data detection relies on static lists of known VPN and proxy servers, as well as basic WHOIS data. But that approach can’t keep up with the ever-evolving nature of the privacy landscape – 41% of privacy IP data changes monthly.
IPinfo, unlike other IP data providers, combines that information with dynamic detection and active verification to ensure superior accuracy. While competitors rely primarily on static lists and basic WHOIS data that quickly become outdated, our approach is fundamentally different:
- Continuous monitoring with our proprietary Probe Network spanning 900+ servers globally
- Active VPN handshake testing that directly confirms VPN protocols on suspected IPs
- Behavioral pattern analysis through mobile device data to detect anomalous connection patterns
- Direct enrollment in 100+ residential proxy services to maintain up-to-date detection capabilities
- Daily refreshed data compared to competitors' weekly or monthly updates
Our data shows:
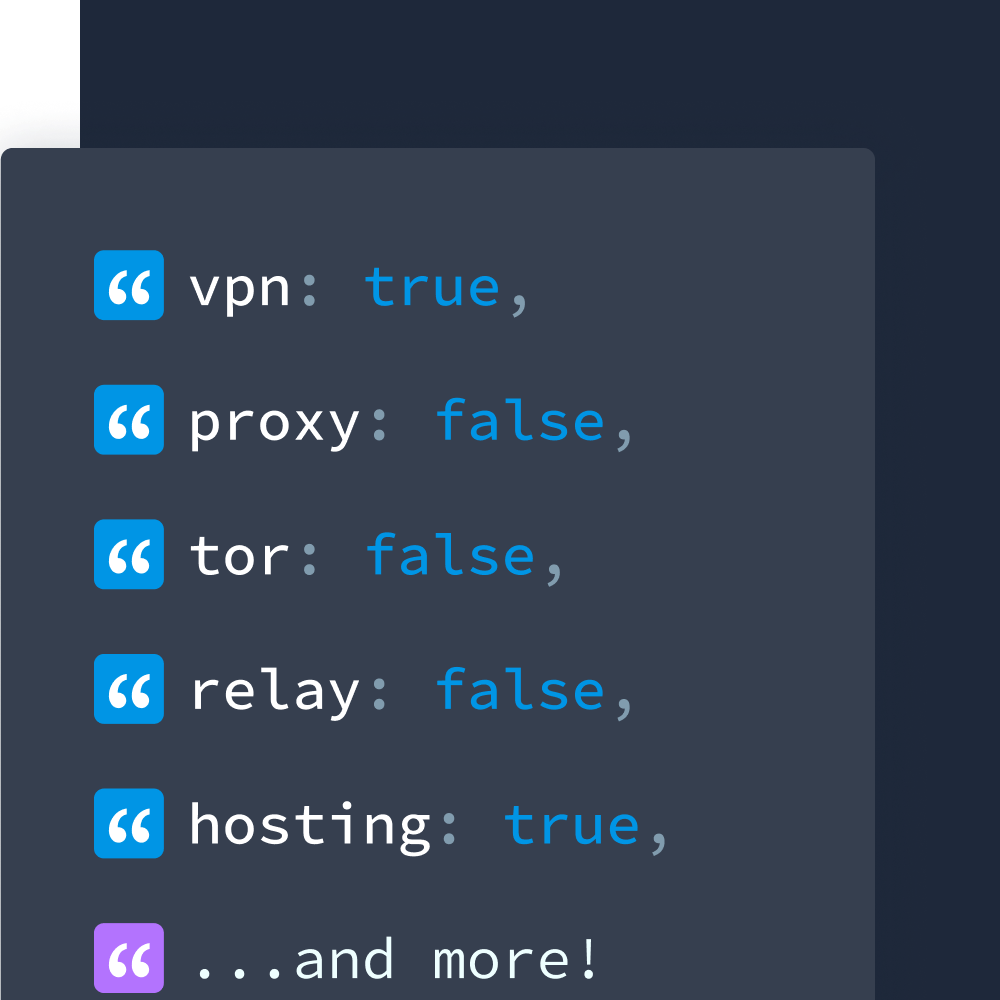
- Whether the IP is associated with a VPN, proxy, Tor, or other obfuscating service
- If an IP address is linked to a known VPN service
- What type of proxy is being used (public, residential, or other)
- What hosting provider the IP belongs to
Experience best-in-class IP privacy data
With IPinfo, discovering IP addresses using anonymization tools is easier than ever.
Privacy Detection Use Cases
Privacy detection data serves a variety of purposes in many different industries:
- Cybersecurity and fraud prevention: Differentiate between legitimate and malicious anonymized traffic to prevent account takeovers, block traffic, and develop risk assessments.
- Compliance with digital and regional regulations: Determine when users are trying to hide their true locations in order to enforce licensing restrictions, comply with local laws, and protect important accounts.
- Ecommerce: Ensure that transactions are valid by matching IP locations to billing addresses, implementing risk-based authentication, and applying specialized policies for traffic from privacy services.
- Fintech: Protect financial assets by identifying potentially fraudulent transactions, implementing additional security measures for high-risk connections, and prevent the bypassing of geographic restrictions.
- Gametech: Make game play a more engaging experience by identifying suspicious connections, protecting gaming ecosystems from coordinated attacks, and maintaining appropriate regional pricing models.
- Adtech: Improve ad spend ROI by filtering out suspicious traffic, excluding fraudulent clicks and impressions, and delivering accurate analytics.
Ready to delve even deeper into use cases, the future of privacy data, and more? Read our ebook The Essential Guide to Anonymous IPs and Privacy Detection Data.
The Challenges of Accurate Privacy Detection
While identifying anonymized IPs is crucial, it comes with inherent challenges. Traditional methods often struggle with:
- False positives: Incorrectly flagging legitimate traffic as anonymized, potentially blocking valid users
- False negatives: Missing sophisticated anonymization methods, leaving security gaps
- Rapidly changing IP landscapes: Privacy networks constantly rotate IPs to evade detection
- Distinguishing between legitimate and malicious use: The same technology serves both privacy advocates and bad actors
IPinfo addresses these challenges by providing rich contextual data about our detection methods and additional IP metadata such as confidence levels (rated 1-3), detection timestamps, and specific detection methods like census, device_activity, vpn_config, and whois associations. This information empowers users to understand the precise nature of anonymized IPs according to their specific use cases and make nuanced decisions about how to handle potentially anonymized traffic.
This balanced approach maintains high accuracy while minimizing disruption to legitimate users who may be using privacy services for valid reasons, as organizations can implement risk-based policies tailored to their specific tolerance levels and security requirements.
Using IPinfo for IP Privacy Detection
With our unique approach to data accuracy, companies can more easily navigate the muddy waters of identifying masked IP addresses. Our proprietary Probe Network, along with our rigorous data methodology, means we serve as the benchmark for data accuracy.
We’re also constantly evolving our efforts to address emerging challenges in the privacy space, from behavior analysis to risk scoring to research coordination with academic institutions. The stakes are too high to settle for “good enough” data – we aim for excellence.
Get access to industry-leading IP privacy data
Locate users, customize experiences, eliminate site risks, and much more.
About the author

Meghan is the content strategist at IPinfo, where she develops and writes content for users to better understand the value of IP data and IPinfo products.