Get Unlimited Access to IPinfo Lite
Start using accurate IP data for cybersecurity, compliance, and personalization—no limits, no cost.
Sign up for freeAnonymizing IP addresses, or IP masking, is a common technique used to hide user identity, bypass content restrictions, or, unfortunately, to perform fraudulent activities. Among the most widely used tools for IP anonymization are VPNs (virtual private networks) and proxies. Though both are used to mask real IP addresses, they work differently and offer varying levels of security, privacy, and performance.
In this article, we’ll break down how each method works, where they overlap, and why it matters when you’re trying to identify anonymized traffic.
Understanding VPNs and Proxies
First, it’s important to understand how VPNs and proxies work for users, to contextualize the categories of IP data you will encounter using IPinfo’s privacy detection data.
What Is a VPN?
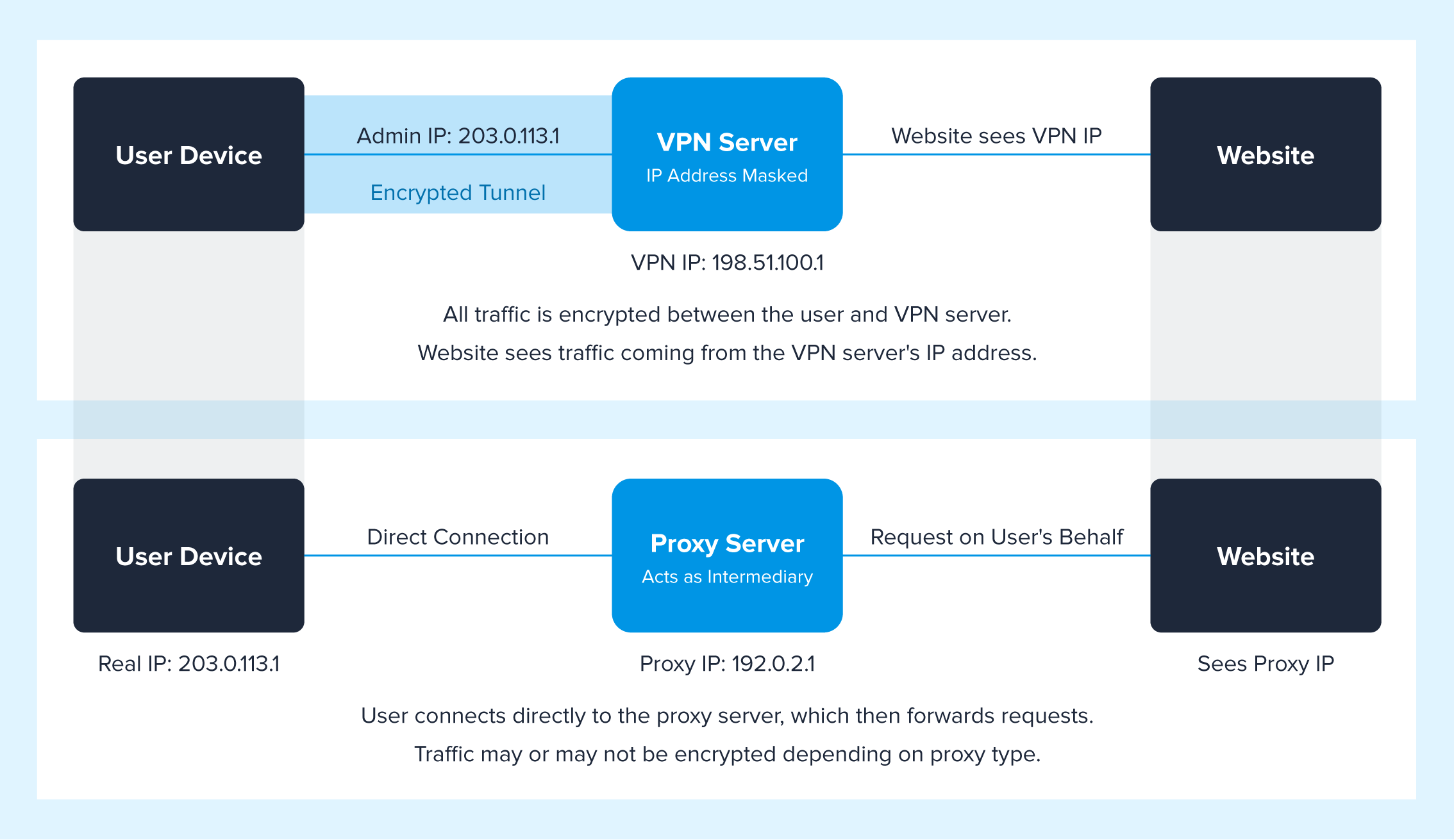
A VPN creates a secure, encrypted connection between a user’s device and a remote server, which is usually operated by the VPN provider.
When connected, all internet traffic is routed through this VPN server. The user’s real IP address is replaced with the VPN’s IP address, often changing where they appear to be geolocated, and their data is encrypted, making it unreadable in transit. That allows users to sidestep geographic restrictions or firewalls and become more anonymous on the internet.
Our privacy detection API flags VPN-based IPs in real time, helping customers detect and act on anonymized traffic.
How VPNs Handle IP Addresses and Data Encryption
VPNs mask a user’s real IP address and encrypt their internet traffic. When connected to a VPN, the user's data is routed through a secure server, which assigns a new IP address based on the server's location. This hides the user's actual IP and helps bypass geographic restrictions or tracking.
To ensure privacy and security, VPNs use encryption protocols like OpenVPN, IKEv2, and WireGuard. These protocols create secure tunnels for data, making it difficult for third parties to trace the original IP address. While this protects user privacy, it also means the IP we detect belongs to the VPN server, not the user's actual device.
Common Use Cases for VPNs
- Privacy and Online Anonymity: VPNs mask real IP addresses, making it difficult to accurately determine a user’s true location, identity, or intent.
- Secure Remote Work: Employees use VPNs to securely access company networks and resources from remote locations, which also reduces IP traceability and complicates threat analysis.
- Bypassing Geo-Restrictions: Users can spoof their location, undermining region-specific content controls and distorting geo-based analytics.
- Protecting Data on Public Wi-Fi: While beneficial for user security, VPNs encrypt traffic in a way that limits visibility into network behaviors.
- Avoiding ISP Throttling: Users can obscure traffic types and patterns, making it harder to differentiate between normal and suspicious activity.
- Secure Online Transactions: VPNs anonymize sensitive sessions, which can help criminals hide behind false locations during fraud attempts.
- Circumventing Censorship: VPNs enable access to restricted content, but also complicate compliance and regional enforcement for regulated services.
- Torrenting: Peer-to-peer activity is obscured, reducing accountability and increasing the difficulty of enforcing copyright protections or detecting abuse.
What Is a Proxy?
A proxy is an intermediary server that sits between a user’s device and the internet, routing traffic on the user's behalf. When a user connects to a proxy, their requests are first sent to the proxy server, which then forwards those requests to the destination website or service. The response is returned to the proxy, which sends it back to the user. This setup hides the user's real IP address, making it appear as though the traffic is coming from the proxy server.
Some proxies offer basic masked IPs, while others include features like caching for faster access or filtering for security and content control. However, unlike VPNs, proxies typically don’t encrypt traffic, which makes them less secure for sensitive data.
Types of Proxies
At IPinfo, we identify two main types of proxies based on distinct patterns, such as high volumes of traffic from single IP blocks and non-typical geolocation markers:
- Datacenter proxies: Hosted in cloud providers or dedicated server farms with IP ranges easily identifiable as non-residential. These are more common but easier to detect and block.
- Residential proxies: Route traffic through regular consumer ISP connections, making them appear as legitimate residential users. These are more difficult to detect as they use IPs assigned to real households.
How Proxies Handle IP Addresses and Data Transmission
Proxies assist with IP masking and data forwarding by acting as intermediaries between a user’s device and the internet. When a user sends a request through a proxy, the proxy server replaces the user’s IP address with its own before forwarding the request to the destination server. However, unlike VPNs, most proxies do not encrypt the data being transmitted. They simply pass information between the user and the web server without securing it, which means any sensitive data could potentially be exposed.
Common Use Cases for Proxies
- Online Anonymity: Proxies mask real IPs, making it difficult to identify true user locations or behaviors.
- Bypassing Geo-Restrictions: Users can mislead streaming services into delivering region-locked content to users outside permitted areas.
- Web Scraping or Data Collection: Proxy networks are frequently used to automate large-scale data scraping, often violating terms of service.
- Ad Verification: Some businesses use proxies to view ads as users in different regions would, but proxies can also be used to commit click fraud.
- Brand Protection: Brands can anonymously track brand abuse, but proxies can also be misused for impersonation or fraud.
- Load Balancing and Network Optimization: Reverse proxies obscure server infrastructure, complicating IP data analysis.
- Content Filtering and Access Control: It’s easier to distort visibility into user activity and intent.
- Secure Business Operations: Internal proxies can mask device-level details critical for threat detection.
- Avoiding Rate Limits and CAPTCHAs: Proxies are commonly used to evade abuse-prevention systems.
- Testing and Monitoring Websites: Synthetic traffic from proxies can skew analytics and location-based metrics.
- Social Media and SEO: Proxies can be used to manipulate engagement metrics or automate spam, distorting genuine traffic data.
Unmask IPs with Privacy Detection API
IPinfo’s Privacy Detection API identifies IP masking methods like VPNs, proxies, Tor, private relays, and hosting providers that tunnel traffic and hide real IP addresses.
Key Differences Between VPN and Proxy IP Data
The key difference between a VPN and a proxy is encryption. While both hidden IPs route traffic through a remote server, only a VPN encrypts your data, making it unreadable to unauthorized users and offering stronger privacy and security compared to a proxy.
Data Encryption and Security
VPNs provide strong data encryption and security by creating an encrypted tunnel between the user's device and a remote server. They use protocols that rely on advanced encryption methods to protect data in transit, ensuring that even if the traffic is intercepted, it remains unreadable to unauthorized parties. VPNs also often include features like kill switches, DNS leak protection, and multi-factor authentication to further safeguard user privacy and prevent data exposure.
Most proxies do not encrypt traffic. They simply forward data while masking the user’s IP address. This lack of encryption means any data sent through a proxy can be intercepted or monitored, especially on unsecured networks.
IP Address Masking and Anonymity
VPNs mask IP addresses by routing a user’s internet traffic through an encrypted tunnel to a remote server, replacing the user's real IP with that of the VPN server. This makes it appear as though the traffic originates from the VPN server’s location, providing a high level of anonymity and effectively hiding the user's identity and location.
Proxies also mask IP addresses by forwarding requests through an intermediary server. Unlike VPNs, most proxies don’t encrypt traffic, which limits their ability to fully anonymize user behavior.
Data Accessibility and Logging
Some VPN providers often promote strict no-logs policies, meaning they do not record user activity or connection details, enhancing privacy and anonymity, but some may log metadata like connection timestamps or IP addresses, which could potentially be accessed by third parties or government agencies.
Proxies typically have less stringent privacy protections. Many proxy services log user activity, IP addresses, and browsing data, which can be shared with advertisers, sold, or accessed by third parties. Because proxies generally lack encryption and robust privacy safeguards, they pose higher risks for data exposure and tracking.
Performance and Speed
VPNs often impact connection speed due to the encryption overhead involved in securing data between the user and the VPN server. The physical distance to the VPN server can introduce latency, affecting overall speed. However, many modern VPNs optimize performance to minimize this impact.
Proxies, on the other hand, generally offer faster connections since they typically do not encrypt traffic, resulting in lower processing overhead. But they can still experience latency depending on server load, geographic distance, and the type of proxy used.
Access IP Data From Both VPN and Proxy Users
At IPinfo, we specialize in identifying anonymous IP addresses including those masked by VPNs, proxies, and other anonymization tools to provide accurate and reliable IP data. Our approach combines static identification with dynamic detection and active verification methods to distinguish what IP addresses are coming from anonymizing services.
We continuously gather and update information on known VPN servers, proxy endpoints, data centers, and hosting providers. This approach is critical because 10% of privacy IP data changes monthly.
Our process for privacy detection includes:
- Active protocol detection: We scan for VPN and proxy protocols across the entire IPv4 space
- Behavioral analysis: We identify anomalous routing patterns and connection behaviors
- Temporal tracking: We monitor how IPs move in and out of privacy services over time
- Service correlation: We map relationships between IPs and specific anonymization services
Our privacy detection IP data shows:
- Whether the IP is associated with a VPN, proxy, Tor, or other obfuscating service
- If an IP address is linked to a known VPN service
- What type of proxy is being used (public, residential, or other)
- What hosting provider the IP belongs to
- The name of the specific VPN or proxy service
- Confidence scores for each detection
- Historical tracking of when IPs entered or left privacy services
- For residential proxies, we provide percent_days_seen to indicate stability (in data download format only)
- Transparency about how each IP was identified
All of this context allows businesses using privacy detection data to implement proportional responses based on the data they’re seeing.
Access Industry Leading APIs
Find users, personalize experiences, reduce site risks, and more.
Final Thoughts on VPN IP Data vs Proxy Data
VPNs and proxies are widely used to mask real IP addresses, providing privacy and security, but creating challenges for businesses relying on accurate IP data. These tools route traffic through remote servers, often encrypting data or obscuring the user’s true location, which can complicate fraud prevention, content restrictions, and risk assessment.
IPinfo offers sophisticated solutions that help businesses identify and analyze anonymous IPs, including those coming from VPNs and proxies, enabling businesses to maintain accurate geolocation, enforce policies, support zero trust architecture, and improve security. With IPinfo, businesses gain reliable access to critical IP information, empowering smarter, more confident decision-making.
About the author

Meghan is the content strategist at IPinfo, where she develops and writes content for users to better understand the value of IP data and IPinfo products.